|
Site Map FM 34-52 INTELLIGENCE INTERROGATION -- SEPTEMBER 28, 1992 |
|||||||||||||||||||||
|
CHAPTER 3:
THE INTERROGATION PROCESS Criteria for selecting personnel to be interrogated vary with the --
In this regard, source selection is important in conducting interrogation at tactical echelons of command because of the proximity to enemy elements, number and conditions of detainees, and time restrictions. The interrogation process involves screening of sources for interrogation and the use of interrogation techniques and procedures. Screening and interrogation involve complex interpersonal skills, and many aspects of their performance are subjective. Each screening and interrogation is unique because of the interaction between the interrogator and the source. The five interrogation phases -- planning and preparation, approach, questioning, termination, and reporting -- are discussed later in this chapter. Interrogators are trained to exploit sources and CED. This allows the all-source collection manager three exploitation options for interrogation assets: They may exploit sources alone, exploit CEDs, or exploit both simultaneously. In the past, it was assumed interrogators could accomplish the dual collection mission no matter what type of combat operations were being supported. This may no longer be true. Unit staffing, coupled with the amount of CEDs and sources, may prevent exploitation of sources and CEDs simultaneously. The density of interrogation assets and command emphasis on the collection effort determine mission requirements. The feasibility of a dual collection mission may also be the result of initial IPB by the commander's intelligence staff. If an echelon cannot conduct a dual collection effort, interrogating sources receives the priority for two reasons:
An individual's value system is easier to bypass immediately after undergoing a significant traumatic experience. The circumstances of capture are traumatic for most sources. Many former PWs indicated extreme disorientation immediately after capture. Capture thrusts them into a foreign environment over which they have no control. Their mores were of no use to them during this period. Most of them survived this phase by clinging to very basic values (love of family and loyalty to friends or comrades). Since humans are adaptable, this initial vulnerability passes quickly. An individual's established values begin to assert themselves again within a day or two. When this happens, much of an individual's susceptibility to interrogation is gone. Memory stores information in two areas: short-term and long-term memory. The five senses constantly transmit information to the brain's short-term memory temporarily and then shifts to the brain's long-term memory. The time at which this transfer takes place varies, but research shows a great amount of detail is lost during that transfer. The percentage of information lost beyond recall varies from study to study, but 70 percent is a conservative estimate. Much of the information of value to the interrogator is information the source is not aware he has. Although no research data is available in this area, it is likely this type of information will be lost quickly. CEDs, while not affected by memory loss, are often time-sensitive and thus are screened quickly for possible exploitation (see Chapter 4). The supported echelon's intelligence officer determines the guidelines for priority of exploitation. The commander's intelligence needs and the J2's, G2's, or S2's estimate of the enemy's intentions dictate the extent to which these guidelines can be applied. Exploitation priorities are reviewed and changed when needed. Screening is the selection of sources for interrogation. It must be conducted at every echelon to --
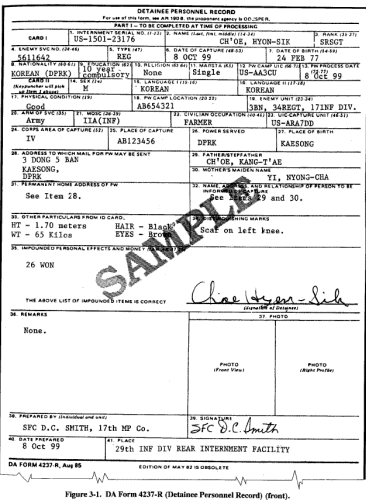
Screeners should obtain a copy of the element's overall objective statement from the PIR, IR, and SIR and become familiar with the intelligence indicators listed there. Screeners must use their experience and imagination to devise ways to identify EPWs and detainees who might possess information pertinent to these indicators. For example, one group of indicators may concern new enemy units moving along a specific avenue of approach. In this case, a screener may want to concentrate first on screening EPWs and detainees captured near that location. When he questions those EPWs or detainees, the screener might try to determine what units are due to arrive in that area in the near future. The ability to recognize branch of service and rank insignia can be of great assistance to screeners. Screeners coordinate with MP holding area guards on their role in the screening process. The guards are told where the screening will take place, how EPWs and detainees are to be brought there from the holding area, and what types of behavior on their part will facilitate the screenings. If time permits, screeners should go to the holding area and examine all available documents pertaining to the EPWs and detainees. They should look for signs that certain EPWs and detainees are willing, or can be induced, to cooperate with the interrogator. Previous screening and interrogation reports and EPW personnel records are important. Interrogation reports identify EPWs and detainees who have been cooperative in the past. Prior screening reports indicate EPWs and detainees who appear cooperative. During EPW inprocessing, MPs prepare a DA Form 4237-R, which is prescribed by AR 190-8. A sample is shown at Figure 3-1. DA Form 4237-R contains additional information not required by the GWS, GPW, and GC, but which the EPWs and detainees may have volunteered during inprocessing. The volunteering of information is one indicator of EPW's or detainee's cooperation. When examining documents, screeners should identify topics on which EPWs and detainees have pertinent information. Screeners should make a note of any documents captured with specific EPWs and detainees that may contain indications of pertinent knowledge and potential cooperation. If time permits, screeners should question holding area personnel about the EPWs and detainees. Since these personnel are in almost constant contact with the EPWs and detainees, their descriptions of specific ones can help identify sources who might answer the supported commander's PIR and IR. Screeners should identify and note those EPWs and detainees whose appearance and behavior indicate they are willing to cooperate immediately or are unlikely to cooperate ever. Unless time is critically short, screeners should --
Before initiating the screening process, the interrogator establishes liaison with supporting CI agents. The CI element, through the CM&D, provides PIR of CI interest. During the screening process, interrogators identify sources of CI interest. After these sources have been interrogated for any information of immediate tactical value (as needed), they are turned over to Cl. CI is interested in sources who --
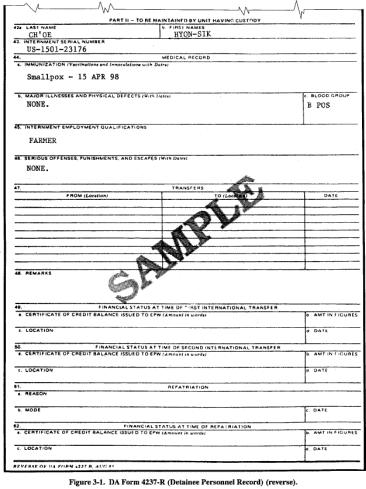
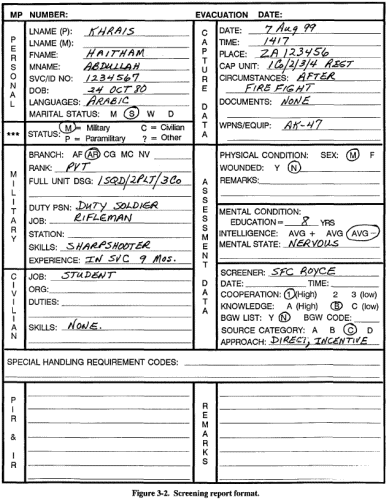
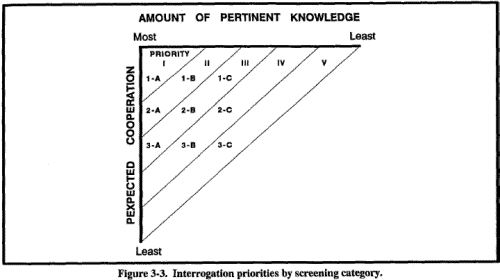
Screeners should always try to screen cooperative knowledgeable EPWs and detainees first. These include EPWs and detainees identified during the screener's review of documents, questioning of holding area personnel, and their own personal observations. Based on screener notes and recommendations, they establish the order which EPWs and detainees will be questioned. The holding area guards are then told to bring these EPWs and detainees, in order, to the screening site one at a time. A screener must use a screening report to record information as it is obtained from the source. Figure 3-2 is a format for a screening report. All information shown is rarely obtained from any one source. The blocks save the screener as much additional writing as possible. If PIR, IR, and SIR information is obtained, it is spot reported in SALUTE formal. When this type of information is obtained during screening, it must be exploited fully and reported as soon as possible. Source screening ends when the screener is sure he can make an accurate assessment of the source's potential cooperation and pertinent knowledge. At this time, the source is returned to the control of the guards, and the screener records his assessment on the screening report. The assessment is recorded using a screening code. The screening code is an alphanumeric designation which reflects the level of cooperation expected from the source and the level of knowledgeability the source may possess. Table 3-1 shows the codes for assessing sources. Those sources who have been assigned to the same category may be interrogated in any order deemed appropriate by the senior interrogator. Category 1A sources normally should be the first to be interrogated; Category 1B, next; followed by those assigned to categories 2A, 1C, 2B, 3A, 2C, and 3B. Category 3C sources are normally interrogated last. This order ensures the highest probability of obtaining the greatest amount of pertinent information within available time. Screening codes may change with the echelon. The higher the echelon, the more time is available to conduct an approach. Figure 3-3 shows the order in which sources will be interrogated. The term "screening category" should not be confused with the categories that are assigned to EPWs and detainees based on their intelligence value. Table 3-1. Instructions for assessing sources.
Figure 3-2. Screening report format. Figure 3-3. Interrogation priorities by screening category. There are five interrogation phases which take place after the screening process.
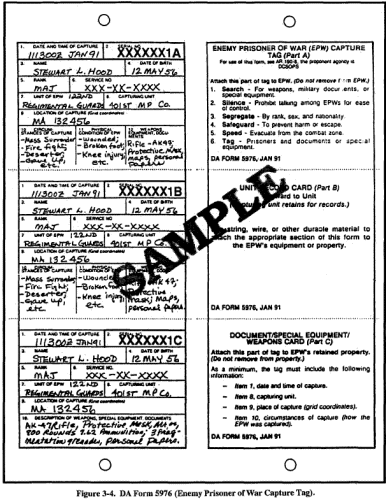
Once the senior interrogator has assigned specific sources to his subordinates, the interrogators develop a plan for their interrogations. These plans reflect the supported commander's PIR, IR, and SIR and current tactical situation. If they do not, subsequent interrogations will not help the element to satisfy its assigned collection mission, and information needed by the supported unit will be missed. Each interrogator, where feasible, begins his preparation by examining the SITMAP, OB data base, and pertinent information contained in the interrogation element's files. Screening reports (Figure 3-2) and DA Form 5976 (Enemy Prisoner of War Capture Tag) are excellent sources of information the interrogator needs. Figure 3-4 shows a sample of DA Form 5976. There should be at least one of these documents available on each EPW and detainee. Additional sources of information may be --
The planning and preparation phase and the approach phase (discussed later) are interrelated. In the planning and preparation phase, the interrogator gathers --
This information helps the interrogator develop a picture of the source and enables him to select approaches most likely to work. There are four primary factors that must be considered when selecting tentative approaches:
Figure 3-4. DA Form 5976 (Enemy Prisoner of War Capture Tag). The interrogation may require the interrogator conduct research to obtain detailed data on a specific geographic area, political group, weapons system, or technical field. In the technical field, TECHINT personnel assist the interrogator. There are various weapons identification guides to assist the interrogator in identifying any weapons mentioned by the source. However, the source should not be shown this guide until he has thoroughly described the items, or has drawn a picture of the weapons. The interrogator may require maps, documents, recording and photographic equipment, screening reports, and other aids to facilitate the interrogation. From these aids, he must select those best suited to accomplish the objective, determine their availability, and arrange for their procurement well in advance of the interrogation. Some aids the interrogator may use are --
The interrogator must consider in advance obstacles and limitations which may affect the interrogation. These obstacles and limitations may include --
Logistical requirements include --
The various staff sections of the supported command may be called upon to furnish the necessary logistical items mentioned above. All support requests will be coordinated with the appropriate staff officer by the EPW or detainee camp or collecting point commander. Interrogators should question guards about the sources, time permitting, as part of preparation. Since the guards are in constant contact with the sources, they may be able to provide information on --
Time permitting, each interrogator should unobtrusively observe the source to personally confirm his identity and to check his personal appearance and behavior. After the interrogator has collected all information available about his assigned source, he analyzes it. He looks for indicators of psychological or physical weakness that might make the source susceptible to one or more approaches, which facilitates his approach strategy. He also uses the information he collected to identify the type and level of knowledge possessed by the source pertinent to the element's collection mission. The interrogator uses his estimate of the type and extent of knowledge possessed by the source to modify the basic topical sequence of questioning. He selects only those topics in which he believes the source has pertinent knowledge. In this way, the interrogator refines his element's overall objective into a set of specific interrogation subjects. The major topics that can be covered in an interrogation are shown below in their normal sequence. However, the interrogator is free to modify this sequence as necessary.
As a result of the planning and preparation phase, the interrogator develops a plan for conducting his assigned interrogation. He must review this plan with the senior interrogator, when possible. Whether written or oral, the interrogation plan must contain at least the following items:
The senior interrogator reviews each plan and makes any changes he feels necessary based on the commander's PIR and IR. After the plan is approved, the holding compound is notified when to bring the source to the interrogation site. The interrogator collects all available interrogation aids needed (maps, charts, writing tools, and reference materials) and proceeds to the interrogation site. The approach phase begins with initial contact between the EPW or detainee and interrogator. Extreme care is required since the success of the interrogation hinges, to a large degree, on the early development of the EPW's or detainee's willingness to communicate. The interrogator's objective during this phase is to establish EPW or detainee rapport, and to gain his willing cooperation so he will correctly answer pertinent questions to follow. The interrogator --
The amount of time spent on this phase will mostly depend on the probable quantity and value of information the EPW or detainee possesses, the availability of other EPW or detainee with knowledge on the same topics, and available time. At the initial contact, a businesslike relationship should be maintained. As the EPW or detainee assumes a cooperative altitude, a more relaxed atmosphere may be advantageous. The interrogator must carefully determine which of the various approach techniques to employ. Regardless of the type of EPW or detainee and his outward personality, he does possess weaknesses which, if recognized by the interrogator, can be exploited. These weaknesses are manifested in personality traits such as speech, mannerisms, facial expressions, physical movements, excessive perspiration, and other overt indications that vary from EPW or detainee. From a psychological standpoint, the interrogator must be cognizant of the following behaviors. People tend to --
Interrogators do not "run" an approach by following a set pattern or routine. Each interrogation is different, but all interrogation approaches have the following in common. They --
The successful application of approach techniques eventually induces the source to willingly provide accurate intelligence information to the interrogator. The term "willingly" refers to the source's answering the interrogator's questions, not necessarily his cooperation. The source may or may not be aware he is providing the interrogator with information about enemy forces. Some approaches may be complete when the source begins to answer questions. Others may have to be constantly maintained or reinforced throughout the interrogation. The techniques used in an approach can best he defined as a series of events, not just verbal conversation between the interrogator and the source. The exploitation of the source's emotion can he harsh or gentle in application. Some useful techniques used by interrogators are --
There are two types of rapport postures determined during planning and preparation: stern and sympathetic. In the stern posture, the interrogator keeps the EPW or detainee at attention. The aim is to make the EPW or detainee keenly aware of his helpless and inferior status. Interrogators use this posture with officers, NCOs, and security-conscious enlisted men. In the sympathetic posture, the interrogator addresses the EPW or detainee in a friendly fashion, striving to put him at ease. This posture is commonly used In interrogating older or younger EPWs. EPWs may he frightened and confused. One variation of this posture is when the interrogator asks about the EPW's family. Few EPWs will hesitate to discuss their family. Frightened persons, regardless of rank, will invariably talk in order to relieve tension once they hear a sympathetic voice in their own tongue. To put the EPW at ease, the interrogator may allow the EPW to sit down, offer a cigarette, ask whether or not he needs medical care, and otherwise show interest in his case. There are many variations of these basic postures. Regardless of the one used, the interrogator must present a military appearance and show character and energy. The interrogator must control his temper at all times, except when a display is planned. The interrogator must not waste time in pointless discussions or make promises he cannot keep; for example, the interrogator's granting political asylum. When making promises in an effort to establish rapport, great care must be taken to prevent implying that rights guaranteed the EPW under international and US law will be withheld if the EPW refuses to cooperate. Under no circumstances will the interrogator betray surprise at anything the EPW might say. Many EPWs will talk freely if they feel the information they are discussing is already known to the interrogator. If the interrogator acts surprised, the EPW may stop talking immediately. The interrogator encourages any behavior that deepens rapport and increases the flow of communication. At the same time, the interrogator must discourage any behavior that has the opposite effect. The interrogator must always be in control of the interrogation. If the EPW or detainee challenges this control, the interrogator must act quickly and firmly. Everything the interrogator says and does must be within the limits of the GPW, Article 17. Rapport must be maintained throughout the interrogation, not only in the approach phase. If the interrogator has established good rapport initially and then abandons the effort, the source would rightfully assume the interrogator cares less and less about him as the information is being obtained. If this occurs, rapport is lost and the source may cease answering questions. Rapport may be developed by --
Depending on the situation, and requests the source may have made, the interrogator also can use the following to develop rapport.
After having established control and rapport, the interrogator continually assesses the source to see if the approaches -- and later the questioning techniques -- chosen in the planning and preparation phase will indeed work. Approaches chosen in planning and preparation are tentative and based on the sometimes scanty information available from documents, guards, and personal observation. This may lead the interrogator to select approaches which may be totally incorrect for obtaining this source's willing cooperation. Thus, careful assessment of the source is critical to avoid wasting valuable time in the approach phase. The questions can be mixed or separate. If, for example, the interrogator has tentatively chosen a "love of comrades" approach, he should ask the source questions like "How did yon get along with your fellow squad members?" If the source answers they were all very close and worked well as a team, the interrogator can use this approach and be reasonably sure of its success. However, if the source answers, "They all hated my guts and I couldn't stand any of them," the interrogator should abandon that approach and ask some quick, nonpertinent questions to give himself time to work out a new approach. The interrogator must guide the conversation smoothly and logically, especially if he needs to move from one approach technique to another. "Poking and hoping" in the approach may alert the prisoner to ploys and will make the job more difficult. Tie-ins to another approach can be made logically and smoothly by using transitional phrases. Logical tie-ins can be made by including simple sentences which connect the previously used approach with the basis for the next one. Transitions can also be smoothly covered by leaving the unsuccessful approach and going back to nonpertinent questions. By using nonpertinent conversation, the interrogator can move the conversation in the desired direction and, as previously stated, sometimes can obtain leads and hints about the source's stresses or weaknesses or other approach strategies that may be more successful. If an interrogator is using argument and reason to get the source to cooperate, he must be convincing and appear sincere. All inferences of promises, situations, and arguments, or other invented material must be believable. What a source may or may not believe depends on the interrogator's knowledge, experience, and training. A good source assessment is the basis for the approach and vital to the success of the interrogation effort. Every source has a breaking point, but an interrogator never knows what it is until it has been reached. There are, however, some good indicators the source is near his breaking point or has already reached it. For example, if during the approach, the source leans forward with his facial expression indicating an interest in the proposal or is more hesitant in his argument, he is probably nearing the breaking point. The interrogator must be alert to recognize these signs. Once the interrogator determines the source is breaking, he should interject a question pertinent to the objective of the interrogation. If the source answers it, the interrogator can move into the questioning phase. If the source does not answer or balks at answering it, the interrogator must realize the source was not as close to the breaking point as thought. In this case, the interrogator must continue with his approach, or switch to an alternate approach or questioning technique and continue to work until he feels the source is near breaking. The interrogator can tell if the source has broken only by interjecting pertinent questions. This process must be followed until the EPW or detainee begins to answer pertinent questions. It is possible the EPW or detainee may cooperate for a while and then balk at answering further questions. If this occurs, the interrogator can reinforce the approaches that initially gained the source's cooperation or move into a different approach before returning to the questioning phase. At this point, it is important to note the amount of time spent with a particular source depends on several factors:
The number of approaches used is limited only by the interrogator's skill. Almost any ruse or deception is usable as long as the provisions of the GPW, as outlined in Figure 1-4, are not violated. An interrogator must not pass himself off as a medic, chaplain, or as a member of the Red Cross (Red Crescent or Red Lion). To every approach technique, there are literally hundreds of possible variations, each of which can be developed for a specific situation or source. The variations are limited only by the interrogator's personality, experience, ingenuity, and imagination. With the exception of the direct approach, no other approach is effective by itself. Interrogators use different approach techniques or combine them into a cohesive, logical technique. Smooth transitions, sincerity, logic, and conviction almost always make a strategy work. The lack of will undoubtedly dooms it to failure. Some examples of combinations are --
The number of combinations are unlimited. Interrogators must carefully choose the approach strategy in the planning and preparation phase and listen carefully to what the source is saying (verbally or nonverbally) for leads the strategy chosen will not work. When this occurs, the interrogator must adapt to approaches he believes will work in gaining the source's cooperation. The approach techniques are not new nor are all the possible or acceptable techniques discussed below. Everything the interrogator says and does must be in concert with the GWS, GPW, GC, and UCMJ. The approaches which have proven effective are --
The interrogator asks questions directly related to information sought, making no effort to conceal the interrogation's purpose. The direct approach, always the first to be attempted, is used on EPWs or detainees who the interrogator believes will cooperate. This may occur when interrogating an EPW or detainee who has proven cooperative during initial screening or first interrogation. It may also be used on those with little or no security training. The direct approach works best on lower enlisted personnel, as they have little or no resistance training and have had minimal security training. The direct approach is simple to use, and it is possible to obtain the maximum amount of information in the minimum amount of time. It is frequently employed at lower echelons when the tactical situation precludes selecting other techniques, and where the EPW's or detainee's mental state is one of confusion or extreme shock. Figure C3 contains sample questions used in direct questioning. The direct approach is the most effective. Statistics show in World War II, it was 90 percent effective. In Vietnam and OPERATIONS URGENT FURY, JUST CAUSE, and DESERT STORM, it was 95 percent effective. The incentive approach is based on the application of inferred discomfort upon an EPW or detainee who lacks willpower. The EPW or detainee may display fondness for certain luxury items such as candy, fruit, or cigarettes. This fondness provides the interrogator with a positive means of rewarding the EPW or detainee for cooperation and truthfulness, as he may give or withhold such comfort items at his discretion. Caution must be used when employing this technique because --
The GPW, Article 41, requires the posting of the convention contents in the EPW's own language. This is an MP responsibility. Incentives must seem to be logical and possible. An interrogator must not promise anything that cannot be delivered. Interrogators do not make promises, but usually infer them while sidestepping guarantees. For example, if an interrogator made a promise he could not keep and he or another interrogator had to talk with the source again, the source would not have any trust and would probably not cooperate. Instead of clearly promising a certain thing, such as political asylum, all interrogator will offer to do what he can to help achieve the source's desired goal, as long as the source cooperates. As with developing rapport, the incentive approach can be broken down into two incentives. The determination rests on when the source expects to receive the incentive offered.
Through EPW or detainee observation, the interrogator can often identify dominant emotions which motivate. The motivating emotion may be greed, love, hate, revenge, or others. The interrogator employs verbal and emotional ruses in applying pressure to the EPW's or detainee's dominant emotions. One major advantage of this technique is it is versatile and allows the interrogator to use the same basic situation positively and negatively. For example, this technique can be used on the EPW who has a great love for his unit and fellow soldiers. The interrogator may take advantage of this by telling the EPW that by providing pertinent information, he may shorten the war or battle in progress and save many of his comrades' lives, but his refusal to talk may cause their deaths. This places the burden on the EPW or detainee and may motivate him to seek relief through cooperation. Conversely, this technique can also be used on the EPW or detainee who hates his unit because it withdrew and left him to be captured, or who feels he was unfairly treated in his unit. In such cases, the interrogator can point out that if the EPW cooperates and specifies the unit's location, the unit can be destroyed, thus giving the EPW an opportunity for revenge. The interrogator proceeds with this method in a very formal manner. This approach is likely to be effective with the immature and timid EPW. Emotional Love Approach. For the emotional love approach to be successful, the interrogator must focus on the anxiety felt by the source about the circumstances in which he finds himself. The interrogator must direct the love the source feels toward the appropriate object: family, homeland, or comrades. If the interrogator can show the source what the source himself can do to alter or improve his situation, the approach has a chance of success. This approach usually involves some incentive such as communication with the source's family or a quicker end to the war to save his comrades' lives. A good interrogator will usually orchestrate some futility with an emotional love approach to hasten the source's reaching the breaking point. Sincerity and conviction are critical in a successful attempt at an emotional love approach as the interrogator must show genuine concern for the source, and for the object at which the interrogator is directing the source's emotion. If the interrogator ascertains the source has great love for his unit and fellow soldiers, the interrogator can effectively exploit the situation. This places a burden on the source and may motivate him to seek relief through cooperation with the interrogator. Emotional Hate Approach. The emotional hate approach focuses on any genuine hate, or possibly a desire for revenge, the source may feel. The interrogator must ascertain exactly what it is the source may hate so the emotion can be exploited to override the source's rational side. The source may have negative feelings about his country's regime, immediate superiors, officers in general, or fellow soldiers. This approach is usually most effective on members of racial or religious minorities who have suffered discrimination in military and civilian life. If a source feels he has been treated unfairly in his unit, the interrogator can point out that, if the source cooperates and divulges the location of that unit, the unit can be destroyed, thus affording the source revenge. By using a conspiratorial tone of voice, the interrogator can enhance the value of this technique. Phrases, such as "You owe them no loyalty for the way they treated you," when used appropriately, can expedite the success of this technique. Do not immediately begin to berate a certain facet of the source's background or life until your assessment indicates the source feels a negative emotion toward it. The emotional hate approach can be used more effectively by drawing out the source's negative emotions with questions that elicit a thought-provoking response. For example, "Why do you think they allowed you to be captured?" or "Why do you think they left you to die?" Do not berate the source's forces or homeland unless certain negative emotions surface. Many sources may have great love for their country, but may hate the regime in control. The emotional hate approach is most effective with the immature or timid source who may have no opportunity up to this point for revenge, or never had the courage to voice his feelings. The fear-up approach is the exploitation of a source's preexisting fear during the period of capture and interrogation. The approach works best with young, inexperienced sources, or sources who exhibit a greater than normal amount of fear or nervousness. A source's fear may be justified or unjustified. For example, a source who has committed a war crime may justifiably fear prosecution and punishment. By contrast, a source who has been indoctrinated by enemy propaganda may unjustifiably fear that he will suffer torture or death in our hands if captured. This approach has the greatest potential to violate the law of war. Great care must be taken to avoid threatening or coercing a source which is in violation of the GPW, Article 17. It is critical the interrogator distinguish what the source fears in order to exploit that fear. The way in which the interrogator exploits the source's fear depends on whether the source's fear is justified or unjustified. Fear-Up (Harsh). In this approach, the interrogator behaves in an overpowering manner with a loud and threatening voice. The interrogator may even feel the need to throw objects across the room to heighten the source's implanted feelings of fear. Great care must be taken when doing this so any actions would not violate the prohibition on coercion and threats contained in the GPW, Article 17. This technique is to convince the source he does indeed have something to fear; that he has no option but to cooperate. A good interrogator will implant in the source's mind that the interrogator himself is not the object to be feared, but is a possible way out of the trap. Use the confirmation of fear only on sources whose fear is justified. During this approach, confirm to the source that he does indeed have a legitimate fear. Then convince the source that you are the source's best or only hope in avoiding or mitigating the object of his fear, such as punishment for his crimes. You must take great care to avoid promising actions that are not in your power to grant. For example, if the source has committed a war crime, inform the source that the crime has been reported to the appropriate authorities and that action is pending. Next inform the source that, if he cooperates and tells the truth, you will report that he cooperated and told the truth to the appropriate authorities. You may add that you will also report his lack of cooperation. You may not promise that the charges against him will be dismissed because you have no authority to dismiss the charges. Fear-Up (Mild). This approach is better suited to the strong, confident type of interrogator; there is generally no need to raise the voice or resort to heavy-handed, table-banging. For example, capture may be a result of coincidence -- the soldier was caught on the wrong side of the border before hostilities actually commenced (he was armed, he could be a terrorist) -- or as a result of his actions (he surrendered contrary to his military oath and is now a traitor to his country, and his forces will take care of the disciplinary action). The fear-up (mild) approach must be credible. It usually involves some logical incentive. In most cases, a loud voice is not necessary. The actual fear is increased by helping the source realize the unpleasant consequences the facts may cause and by presenting an alternative, which, of course, can be brought about by answering some simple questions. The fear-up (harsh) approach is usually a dead end, and a wise interrogator may want to keep it in reserve as a trump card. After working to increase the source's fear, it would be difficult to convince him everything will be all right if the approach is not successful. This technique is nothing more than calming the source and convincing him he will be properly and humanely treated, or telling him the war for him is mercifully over and he need not go into combat again. When used with a soothing, calm tone of voice, this often creates rapport and usually nothing else is needed to get the source to cooperate. While calming the source, it is a good idea to stay initially with nonpertinent conversation and to avoid the subject which has caused the source's fear. This works quickly in developing rapport and communication, as the source will readily respond to kindness. When using this approach, it is important the interrogator relate to the source at his perspective level and not expect the source to come up to the interrogator's level. If the EPW or detainee is so frightened he has withdrawn into a shell or regressed to a less threatening state of mind, the interrogator must break through to him. The interrogator can do this by putting himself on the same physical level as the source; this may require some physical contact. As the source relaxes and begins to respond to kindness, the interrogator can begin asking pertinent questions. This approach technique may backfire if allowed to go too far. After convincing the source he has nothing to fear, he may cease to be afraid and may feel secure enough to resist the interrogator's pertinent question. If this occurs, reverting to a harsher approach technique usually will bring the desired result quickly. The fear-down approach works best if the source's fear is unjustified. During this approach, take specific actions to reduce the source's unjustified fear. For example, if the source believes that he will be abused while in your custody, make extra efforts to ensure that the source is well cared for, fed, and appropriately treated. Once the source is convinced that he has no legitimate reason to fear you, he will be more inclined to cooperate. The interrogator is under no duty to reduce a source's unjustified fear. The only prohibition is that the interrogator may not say or do anything that directly or indirectly communicates to the source that he will be harmed unless he provides the requested information. These applications of the fear approach may be combined to achieve the desired effect. For example, if a source has justified and unjustified fears, you may initially reduce the source's unfounded fears, then confirm his legitimate fears. Again, the source should be convinced the interrogator is his best or only hope in avoiding or mitigating the object of his fear. The strategy of this approach is to trick the source into revealing desired information by goading or flattering him. It is effective with sources who have displayed weakness or feelings of inferiority. A real or imaginary deficiency voiced about the source, loyalty to his organization, or any other feature can provide a basis for this technique. The interrogator accuses the source of weakness or implies he is unable to do a certain thing. This type of source is also prone to excuses and reasons why he did or did not do a certain thing, often shifting the blame to others. An example is opening the interrogation with the question, 'Why did you surrender so easily when you could have escaped by crossing the nearby ford in the river?" The source is likely to provide a basis for further questions or to reveal significant intelligence information if he attempts to explain his surrender in order to vindicate himself. He may give an answer such as, "No one could cross the ford because it is mined." This technique can also be employed in another manner -- by flattering the source into admitting certain information in order to gain credit. For example, while interrogating a suspected saboteur, the interrogator states: 'This was a smooth operation. I have seen many previous attempts fail. I bet you planned this. Who else but a clever person like you would have planned it? When did you first decide to do the job?' This technique is especially effective with the source who has been looked down upon by his superiors. The source has the opportunity to show someone he is intelligent. A problem with the pride and ego approach is it relies on trickery. The source will eventually realize he has been tricked and may refuse to cooperate further. If this occurs, the interrogator can easily move into a fear-up approach and convince the source the questions he has already answered have committed him, and it would be useless to resist further. The interrogator can mention it will be reported to the source's forces that he has cooperated fully with the enemy, will be considered a traitor, and has much to fear if he is returned to his forces. This may even offer the interrogator the option to go into a love-of-family approach where the source must protect his family by preventing his forces from learning of his duplicity. or collaboration. Telling the source you will not report that he talked or that he was a severe discipline problem is an incentive that may enhance the effectiveness of the approach. Pride and Ego-Up Approach. This approach is most effective on sources with little or no intelligence, or on those who have been looked down upon for a long time. It is very effective on low-ranking enlisted personnel and junior grade officers, as it allows the source to finally show someone he does indeed have some "brains." The source is constantly flattered into providing certain information in order to gain credit. The interrogator must take care to use a flattering somewhat-in-awe tone of voice, and speak highly of the source throughout this approach. This quickly produces positive feelings on the source's part, as he has probably been looking for this type of recognition all of his life. The interrogator may blow things out of proportion using items from the source's background and making them seem noteworthy or important. As everyone is eager to hear praise, the source will eventually reveal pertinent information to solicit more laudatory comments from the interrogator. Effective targets for a successful pride and ego-up approach are usually the socially accepted reasons for flattery, such as appearance and good military bearing. The interrogator should closely watch the source's demeanor for indications the approach is working. Some indications to look for are --
Pride and Ego-Down Approach. This approach is based on attacking the source's sense of personal worth. Any source who shows any real or imagined inferiority or weakness about himself, loyalty to his organization, or captured under embarrassing circumstances, can be easily broken with this approach technique.
The objective is for the interrogator to pounce on the source's sense of pride by attacking his loyalty, intelligence, abilities, leadership qualities, slovenly appearance, or any other perceived weakness. This will usually goad the source into becoming defensive, and he will try to convince the interrogator he is wrong. In his attempt to redeem. his pride, the source will usually involuntarily provide pertinent information in attempting to vindicate himself. A source susceptible to this approach is also prone to make excuses and give reasons why he did or did not do a certain thing, often shifting the blame to others. If the interrogator uses a sarcastic, caustic tone of voice with appropriate expressions of distaste or disgust, the source will readily believe him. Possible targets for the pride and ego-down approach are the source's --
The pride and ego-down approach is also a dead end in that, if unsuccessful, it is difficult for the interrogator to recover and move to another approach and reestablish a different type of rapport without losing all credibility. In this approach, the interrogator convinces the source that resistance to questioning is futile. When employing this technique, the interrogator must have factual information. These facts are presented by the interrogator in a persuasive, logical manner. He should be aware of and able to exploit the source's psychological and moral weaknesses, as well as weaknesses inherent in his society. The futility approach is effective when the interrogator can play on doubts that already exist in the source's mind. There are different variations of the futility approach. For example:
If the source's unit had run out of supplies (ammunition, food, or fuel), it would be somewhat easy to convince him all of his forces are having the same logistical problems. A soldier who has been ambushed may have doubts as to how he was attacked so suddenly. The interrogator should be able to talk him into believing that the interrogator's forces knew of the EPW's unit location, as well as many more units. The interrogator might describe the source's frightening recollections of seeing death on the battlefield as an everyday occurrence for his forces. Factual or seemingly factual information must be presented in a persuasive, logical manner, and in a matter-of-fact tone of voice. Making the situation appear hopeless allows the source to rationalize his actions, especially if that action is cooperating with the interrogator. When employing this technique, the interrogator must not only have factual information but also be aware of and exploit the source's psychological, moral, and sociological weaknesses. Another way of using the futility approach is to blow things out of proportion. If the source's unit was low on, or had exhausted, all food supplies, he can be easily led to believe all of his forces had run out of food. If the source is hinging on cooperating, it may aid the interrogation effort if he is told all the other sources have cooperated. The futility approach must be orchestrated with other approach techniques (for example, love of comrades). A source who may want to help save his comrades' lives may be convinced the battlefield situation is hopeless and they will die without his assistance. The futility approach is used to paint a bleak picture for the prisoner, but it is not effective in and of itself in gaining the source's cooperation. This approach may be employed in conjunction with the "file and dossier" technique (discussed below) or by itself. If used alone, the interrogator must first become thoroughly familiar with available data concerning the source. To begin the interrogation, the interrogator asks questions based on this known data. When the source hesitates, refuses to answer, or provides an incorrect or incomplete reply, the interrogator provides the detailed answer. When the source begins to give accurate and complete information, the interrogator interjects questions designed to gain the needed information. Questions to which answers are already known are also asked to test the source's truthfulness and to maintain the deception that the information is already known. By repeating this procedure, the interrogator convinces the source that resistance is useless as everything is already known. After gaining the source's cooperation, the interrogator still tests the extent of cooperation by periodically using questions to which he has the answers; this is very necessary. If the interrogator does not challenge the source when he is lying, the source will know everything is not known, and he has been tricked. He may then provide incorrect answers to the interrogator's questions. There are some inherent problems with the use of the "we know all" approach. The interrogator is required to prepare everything in detail, which is time consuming. He must commit much of the information to memory, as working from notes may show the limits of the information actually known. The file and dossier approach is used when the interrogator prepares a dossier containing all available information obtained from documents concerning the source or his organization. Careful arrangement of the material within the file may give the illusion it contains more data than is actually there. The file may be padded with extra paper, if necessary. Index tabs with titles such as education, employment, criminal record, military service, and others are particularly effective. The interrogator confronts the source with the dossiers at the beginning of the interrogation and explains intelligence has provided a complete record of every significant happening in the source's life; therefore, it would be useless to resist. The interrogator may read a few selected bits of known data to further impress the source. If the technique is successful, the source will be intimidated by the size of the file, conclude everything is known, and resign himself to complete cooperation. The success of this technique is largely dependent on the naivete of the source, volume of data on the subject, and skill of the interrogator in convincing the source. This approach is especially adaptable to interrogation. The interrogator insists the source has been correctly identified as an infamous individual wanted by higher authorities on serious charges, and he is not the person he purports to be. In an effort to clear himself of this allegation, the source makes a genuine and detailed effort to establish or substantiate his true identity. In so doing, he may provide the interrogator with information and leads for further development. The "establish your identity" approach was effective in Viet Nam with the Viet Cong and in OPERATIONS JUST CAUSE and DESERT STORM. This approach can he used at tactical echelons. The interrogator must be aware if it is used in conjunction with the file and dossier approach, as it may exceed the tactical interrogator's preparation resources. The interrogator should initially refuse to believe the source and insist he is the criminal wanted by the ambiguous higher authorities. This will force the source to give even more detailed information about his unit in order to convince the Interrogator lie is who he says he is. This approach works well when combined with the "futility" or "we know all" approach.
This approach is used to induce cooperation from a hostile source. In one variation of this approach, the interrogator listens carefully to a source's answer to a question, and then repeats the question and answer several times. He does this with each succeeding question until the source becomes so thoroughly bored with the procedure he answers questions fully and candidly to satisfy the interrogator and gain relief from the monotony of this method. The repetition technique must be judiciously used, as it will generally be ineffective when employed against introverted sources or those having great self-control. In fact, it may provide an opportunity for a source to regain his composure and delay the interrogation. In this approach, the use of more than one interrogator or a tape recorder has proven effective. This approach involves a psychological ploy based upon the principles that --
This approach may be used by one or simultaneously by two or more interrogators in questioning the same source. In employing this technique, the interrogator asks a series of questions in such a manner that the source does not have time to answer a question completely before the next one is asked. This confuses the source and he will tend to contradict himself, as he has little time to formulate his answers. The interrogator then confronts the source with the inconsistencies causing further contradictions.
In many instances, the source will begin to talk freely in an attempt to explain himself and deny the interrogator's claims of inconsistencies. In this attempt, the source is likely to reveal more than he intends, thus creating additional leads for further exploitation. This approach may be orchestrated with the pride and ego-down or fear-up approaches. Besides extensive preparation, this approach requires an experienced and competent interrogator, with comprehensive case knowledge and fluency in the source's language. This approach may be successful when used against the nervous or confident source. When employing this technique, the interrogator says nothing to the source, but looks him squarely in the eye, preferably with a slight smile on his face. It is important not to look away from the source but force him to break eye contact first. The source may become nervous, begin to shift in his chair, cross and recross his legs, and look away. He may ask questions, but the interrogator should not answer until he is ready to break the silence. The source may blurt out questions such as, "Come on now, what do you want with me?" When the interrogator is ready to break silence, he may do so with some nonchalant questions such as, "You planned this operation for a long time, didn't you? Was it your idea?" The interrogator must be patient when using this technique. It may appear the technique is not succeeding, but usually will when given a reasonable chance. The idea in using this approach is to get the source away from the atmosphere of an interrogation room or setting. If the interrogator confronts a source who is apprehensive or frightened because of the interrogation environment, this technique may prove effective. In some circumstances, the interrogator may be able to invite the source to a different setting for coffee and pleasant conversation. During the conversation in this more relaxed environment, the interrogator steers the conversation to the topic of interest. Through this somewhat indirect method, he attempts, to elicit the desired information. The source may never realize he is being interrogated. Another example in this approach is an interrogator poses as a compound guard and engages the source in conversation, thus eliciting the desired information. The interrogation effort has two primary goals: To obtain information and to report it. Developing and using good questioning techniques enable the interrogator to obtain accurate and pertinent information by following a logical sequence. The questioning phase starts when the source begins to answer questions pertinent to interrogation objectives. Good questioning techniques must be used throughout the interrogation. The interrogator must know when to use different types of questions. Good questioning techniques enable the interrogator to extract the maximum amount of information in the minimum amount of time. The interrogator must be able to use the following types of questions:
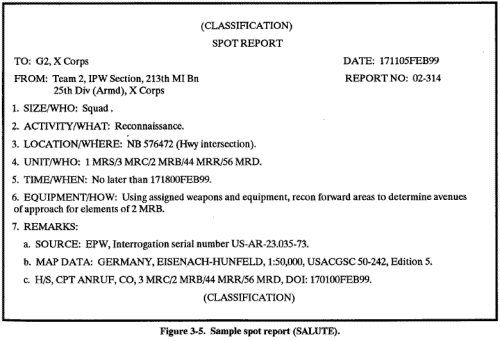
Questions should be presented in a logical sequence to avoid neglecting significant topics. A series of questions following a chronological sequence of events is frequently employed, but this is not the only logical method of asking questions. Adherence to a sequence should not deter the interrogator from exploiting informational leads as they are obtained. The interrogator must consider the probable response of the source to a particular question or line of questioning and should not, if at all possible, ask direct questions likely to evoke a refusal to answer or to antagonize the source. Figure 3-5. Sample spot report (SALUTE). Experience has shown that in most tactical interrogations, the source is cooperative. In such instances, the interrogator should proceed with direct questions. Good, direct questions --
(NOTE: The source may not be on the same intellectual level as the interrogator and some may be illiterate. Some words or phases in English do not translate into a foreign language.) Follow-up questions are used to obtain complete information on a topic that pertains to the interrogation objective. They are used to exploit leads obtained from the source on information not directly related to the primary interrogation objective. Exploitation of these leads is discussed later. There are two types of leads:
Nonpertinent questions are used to conceal the interrogation's objectives or to strengthen rapport with the source. They may also be used to break the source's concentration, particularly, if the interrogator suspects the source is lying. It is hard for a source to be a convincing liar if his concentration is frequently interrupted. Repeated questions ask the source for the same information obtained in response to earlier questions. They may be exact repetitions of the previous question, or the previous question may be rephrased or otherwise disguised. The use of repeated questions may develop a topic the source had refused to talk about earlier. Repeated questions may also be used to --
Control questions are developed from recently confirmed information that is not likely to have changed. They are used to check the truthfulness of the source's responses and should be mixed in with other questions throughout the interrogation. Prepared questions are used primarily when dealing with information of a technical nature, or specific topic, which requires the interrogator to formulate questions beforehand; the interrogator prepares them in writing to be used during the interrogation. The interrogator may have to research technical material or contact TECHINT personnel to assist him in preparing questions. Interrogators must not allow the use of prepared questions to restrict the scope and flexibility of their interrogations. The interrogator must use the different type of questions effectively. Active listening and maximum eye-to-eye contact with the source will provide excellent indicators for when to use follow-up, repeated, control, and nonpertinent questions. The interrogator must use direct and follow-up questions to fully exploit subjects pertinent to his interrogation objectives. He should periodically include control, repeated, and nonpertinent questions in order to check the sincerity and consistency of the source's responses and to strengthen rapport. A response which is inconsistent with earlier responses or the interrogator's available data is not necessarily a lie. When such a response is obtained, the interrogator should reveal the inconsistency to the source and ask for an explanation. The source's truthfulness should then be evaluated based on the plausibility of his explanation. Interrogators should avoid the following types of questions. Leading questions require the source to answer Yes or No. They do not elicit narrative answers. They also prompt the source to answer the question in a way he thinks the interrogator wants to hear it; for example, "Did you go to the command post last night?" Although normally avoided during the interrogation, leading questions may be used to --
Negative questions should never be used during an interrogation. They imply the source should reply in the negative, and this sometimes confuses or leads the source to provide false information; for example, "You're not in the 1st Company, are you?" Negative questions usually require additional questions to clarify the source's responses. Compound questions are never used during an interrogation. They are two questions asked at the same time; for example, "Before you were captured today, were you traveling north or south?" They are easily misunderstood and may confuse the source or force him to give an ambiguous answer. Compound questions allow the source to evade a part of the question or to give an incomplete answer. They may confuse the source or cause the interrogator to misunderstand the response. Vague questions do not have enough information for the source to understand exactly what is being asked by the interrogator. They may be incomplete, general, or otherwise nonspecific and create doubt in the source's mind. Vague questions confuse the source, waste time, are easily evaded, and result in answers that may confuse or mislead the interrogator. An Interrogators Guide is a pamphlet or notebook designed to guide the interrogator through the interrogation. The IPW senior interrogator should ensure team members prepare an interrogators guide, which could be included in the unit's SOP. The guides are made based on the AO and supported command intelligence requirements. They should be jointly prepared by the interrogator and available intelligence analysts. The guides contain information such as --
Spot reportable information is critical to the successful accomplishment of friendly COAs. Information may be spot reportable even when an interrogator cannot determine its immediate intelligence value. Spot reportable information is always time sensitive in that its value depends on the speed with which it is reported and processed. If an interrogator obtains information he thinks is spot reportable, he must compare the information with his element's overall objective statement. Items of information relating to any of the intelligence indicators listed in the objective statement are spot reportable. Information relating to indicators not listed may still be spot reportable. The key to identifying spot reportable information is recognizing its potential value. If the information indicates a significant change in the enemy's capabilities or intentions, it is spot reportable. Information inconsistent with current OB holdings should be spot reported if the inconsistency concerns an important item and the source has given a plausible explanation for it. If an interrogator cannot decide if a piece of information is spot reportable, he should act as though it is. This means he should exploit it fully and record all pertinent information. The interrogator should then consult the senior interrogator for a final determination of the information's value. Spot reportable information is transmitted by the interrogator either written or orally in the SALUTE format (Figure 3-5). Leads are signs which tell the interrogator the source has additional pertinent information that can be obtained through further questioning. Hot and cold leads are provided by a source in response to interrogator questions. A hot lead, when exploited, may obtain spot reportable information. A cold lead, when exploited, may obtain information not spot reportable, but still of intelligence value. The use of follow-up questions to fully exploit hot and cold leads may require an interrogator to cover topics he did not list in his interrogation plan. An interrogator must exploit hot leads as soon as he identifies them. Once the interrogator is sure he has obtained and recorded all the details known to the source, he issues a spot report. The interrogator then resumes his questioning of the source at the same point where the hot lead was obtained. An interrogator should note cold leads as they are obtained, and exploit them fully during his questioning on the topics to which the cold lead apply. Cold leads may expand the scope of the interrogation became they may indicate the source possesses pertinent information in areas not previously selected for questioning. If the interrogator does not fully exploit all cold leads he obtains, he must include information on all leads he did not exploit in his interrogation report. H/S information must include the most precise data possible of its source. This will include --
The interrogator begins the questioning phase with the first topic in the sequence he tentatively established as part of his interrogation plan. He obtains all the source's pertinent knowledge in this topical area before moving on to the next topic in his sequence. He maintains his established questioning sequence to ensure no topics are missed. The only exception is exploiting a hot lead. During the questioning phase, the interrogator will attempt to pinpoint locations of any enemy dispositions known to the source. He will attempt to determine the whereabouts of the source, and will compare the source's description of terrain features with maps, aerial photographs, and pictomaps. Some map tracking advantages are --
The interrogator asks the source if he can read the map being used. If so, he should be asked to show the location of routes and dispositions. If the source cannot read the interrogator's map, he must be asked if he knows compass directions. If not, the interrogator must explain them to him. This can be done by having the source picture himself facing the rising or setting sun and then establishing compass points. The interrogator may find the source is most confident when expressing himself in terms other than compass directions. When this happens, the interrogator should allow the source to use his own frames of reference. However, the interrogator must ensure he understands the source. The first location the interrogator should try to establish as the initial common point of reference (ICPR) is the source's POC. The POC cannot be used, however, unless the source can describe it well enough for the interrogator to be certain of its location. If the POC cannot be used, the interrogator must review locations previously mentioned by the source and ask him to describe each of them in turn. Once the source describes a location well enough for the interrogator to be certain of its position on the map, an ICPR has been established. The interrogator then marks that position. The interrogator reviews the source's past missions to identify those points he actually visited. The interrogator determines how long ago the source was at each point, and approximately how far each point is from the ICPR. The interrogator wants to select as the destination common point of reference (DCPR) that point visited by the source which provides the longest route of travel to the ICPR, and is still within the supported command's AI. The DCPR selected must be a location the source can describe well enough for it to be plotted on the map, even if it is nothing more than a general vicinity. The interrogator establishes the route the source traveled between the DCPR and ICPR. When the DCPR is a specific point, the interrogator can establish the route from it to the ICPR, tracing the route in the same direction which the source actually traveled. When the DCPR is an undefined point, the interrogator establishes the route from ICPR to the DCPR. This means the interrogator must trace the route in the opposite direction from that traveled by the source. The interrogator should establish the route traveled by using the following procedures in the sequence shown:
The interrogator can follow the same sequence when establishing the route actually traveled by the source by beginning with the DCPR. The interrogator must obtain the exact location and description of each enemy disposition the source knew about at the DCPR. The interrogator does this by having the source --
The interrogator must repeat these questions, and plot or record the information as it is provided by the source, until he obtains all dispositions known by the source to be in the vicinity of the DCPR. The interrogator begins exploiting the source's route with the segment closest to the ICPR or DCPR. The interrogator will segment closest to the DCPR, but either can be used. The interrogator will exploit each segment of the route by asking the question: "From (description of common point of reference [(CPR)] to (description of next CPR) back along your route of travel, what of military significance belonging to your forces do you know of, have seen, or heard?" The interrogator will continue from segment to segment, fully exploiting each, until he has exploited the entire route traveled. Exploit Dispositions Not on Route If the interrogator obtains a disposition which is not located on the established route, he must establish the route the source would have taken to that disposition. The interrogator then treats this new route the same way he does any other route segment, exploiting it fully before moving on to the next segment of the original route. The sequence above organizes map tracking so information obtained from the source can be plotted and recorded accurately. The description of each disposition must be recorded preferably near the site of the disposition on the map. There are several reasons for recording information obtained during interrogations. The most important is to ensure information can be reported completely and accurately. Recorded information may also be used to --
There are several methods of recording information used during interrogations. Two are listed below, along with their advantages and disadvantages. These methods may be used separately, or in combination with each other. Using His Own Notes. The interrogator's own notes are the primary method of recording information. When the interrogator takes his own notes, he has a ready reference to verify responses to repeated question or to refresh his memory. They also provide him with the means to record cold leads for later exploitation. Using his own notes expedites the interrogator's accurate transferral of information into a report formal when taking his own notes, however, he cannot observe the source continuously. This may cause him to miss leads or fail to detect losses in rapport or control that are detectable only through clues provided by the source's behavior. It is possible to lose control, and the source's willing cooperation, by concentrating too much on note taking. The interrogator must avoid distracting the source while taking notes. They should be taken in such a way that maintains maximum eye-to-eye contact with the source. The interrogator will not have enough time to record each word the source says. Thus, he must --
The only information that should be recorded during the approach phase is that required by Part I of DA Form 4237-R (Figure 3-1). All other Information should not be recorded until after the source's cooperation has been obtained. All notes must be complete, accurate, and legible. Notes should be organized by topical areas. A separate piece of paper should be used to record cold leads. The interrogator should use authorized military abbreviations and brevity codes (see AR 310-50). Notes should be in a recognizable format and complete for other interrogators to use. Situations may arise that require one interrogator to finish another's interrogation. Using a Sound or Video Recorder. This method allows the interrogator to continually observe the source. When compared with note taking, this method allows more information to be obtained In less time. However, more time is required for report writing because the entire tape must be replayed to transfer information to the report. Record names, numbers, and other pertinent, detailed information that may be unclear on the tape. Sound recorders cannot provide a quick reference that can be used to compare answers to a repeated question, and the equipment may malfunction. Another method which has proven successful during exercises is to have linguist qualified intelligence analysts view interrogations or debriefings by using video cameras and monitors. This method allows the intelligence analyst to immediately pass additional questions to the interrogator to follow up on possible source knowledge. When it is necessary or prudent, the interrogator will terminate the Interrogation. There are many ways to conduct a termination, but the following points must be conveyed to the source:
Figure 3-6. DA Form 2662-R (United States Army EPW Identification Card). Some reasons for termination are --
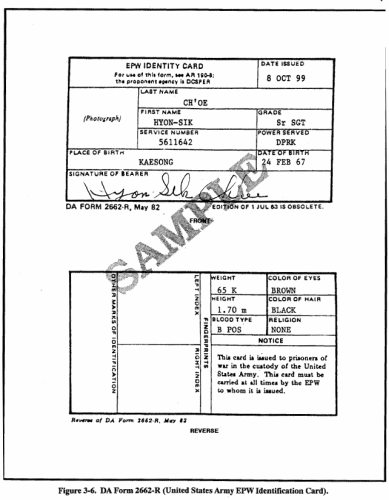
Whatever the reason for terminating, the interrogator must remember there is a possibility someone may want to question the source at a later date. For that reason, he should terminate without any loss of rapport when possible. He offers the opportunity for the source to change or add to any information he has given. During termination, the interrogator must properly dispose of any documents captured with the source. A source's military identity document must be returned to him. If a source does not hold an identity card issued by his government, the MP will issue a DA Form 2662-R (United States Army EPW Identification Card). This form, shown at Figure 3-6, will accompany the source at all times. AR 190-8 is the prescribing directive of this form. Some captured documents will contain information that must be exploited at higher echelons. These documents may be impounded by the interrogator and evacuated through intelligence channels. The interrogator must issue a receipt to the source for any personal documents he decides to impound. He must comply with the accounting procedures established for captured documents by the MP in accordance with AR 190-8. These procedures are time-consuming but necessary. The interrogator can save time by preparing receipts and document tags during the planning and preparation phase. The interrogator completes the termination phase by instructing the escort guard to return the source to the holding compound and to keep him away from sources who have not been interrogated. The last portion of the interrogation process is reporting information obtained. The most brilliantly executed interrogation becomes a wasted effort if not reported properly. To aid military operations, information obtained must be transmitted as quickly as the situation permits in a usable form to an agency capable of taking action. Although the interrogator normally takes notes during the interrogation, he will have to rely all his memory, to some degree, while reporting information received from the source. The more distractions that occur between the interrogation and the reporting, the greater the chance the interrogator will lose some of the information obtained. The reporting normally is done in the format appropriate for the information being reported. Appendix E contains formats of reports. Initial reports are submitted electronically when possible to ensure the information reaches the intelligence analysts in the least amount of time. Written reports are prepared to document electronic reports. They are used as initial means of reporting only when electronic reporting is impossible. Any information of intelligence value that will diminish with the passage of time must be SALUTE reported. Electronic SALUTE reports are formatted and submitted according to the procedures established during the senior interrogator's initial coordination. Information not SALUTE reportable is electronically reported with a lower priority. The aim of any interrogation is to obtain information which will help satisfy a commander's intelligence requirements. Since these requirements will differ in scope at each level, when conducting PIR or IR interrogations, nonapplicable paragraphs may be deleted. Part I must always be included and distribution made according to STANAG 2033. Regardless of the report format used, information must be reported accurately according to the following criteria:
Each report must include the interrogator's assessment of the source's value. This assessment addresses the source's intelligence, experience, cooperation, and reliability. Any areas of special knowledge possessed by the source should be identified. The assessment codes are established by STANAG 2033. The codes assigned, and a written statement supporting these assignments, must be included on each report. INTERROGATION WITH AN INTERPRETER Interrogating through an interpreter is time consuming because the interpreter must repeat everything said by the interrogator and source. The interrogator must brief the interpreter before the interrogation can begin. An interrogation with an interpreter will go through all five phases of the interrogation process. After the interrogation is over, the interrogator will evaluate the interpreter. During the planning and preparation phase, the interrogator selects a method of interpretation. There are two methods: Simultaneous and alternate. The interrogator obtains information about his interpreter from the senior interrogator. He analyzes this information and talks to the interpreter before deciding which method to use. With the alternate method, the interpreter listens to an entire phrase, sentence, or paragraph. He then translates during natural pauses in the interrogation. The simultaneous method should be selected only if all the following criteria are met:
With the simultaneous method, the interpreter listens and translates at the same time as the person for whom he is interpreting, usually just a phrase or a few words behind. If any of the criteria in the simultaneous method cannot be met, the interrogator must use the alternate method. The alternate method should also be used when a high degree of precision is required. Once the interrogator has chosen a method of interpretation, he must brief his interpreter. This briefing must cover --
Throughout the briefing, the interrogator fully and clearly answers questions the interpreter may have. This helps ensure the interpreter completely understands his role in the interrogation. During the interrogation, the interrogator corrects the interpreter if he violates any standards on which he was briefed. For example, if the interpreter injects his own ideas into the interrogation, he must be corrected. Corrections should be made in a low-key manner. At no time should the interrogator rebuke his interpreter sternly or loudly while they are with the source. The interrogator should never argue with the interpreter in the presence of the source. If a major correction must be made, the interrogator and interpreter should leave the interrogation site temporarily, and only when necessary. When initial source contact is made, the interpreter must instruct him to maintain eye contact with the interrogator. Since rapport and control must be established, the interpreter should be able to closely imitate the attitude, behavior, and tone of voice used by the interrogator and source. The questioning phase is conducted in the same way it would be if no interpreter were used. During the termination phase, too, the interpreter's ability to closely imitate the interrogator and source is important. The approaches used are reinforced, and necessary sincerity and conviction must be conveyed to the source. The interpreter assists the interrogator in preparing reports. He may be able to fill in gaps and unclear areas in the interrogator's notes. He may also assist in transliterating, translating, and explaining foreign terms. After submitting all reports, the interrogator evaluates the performance of his interpreter. The evaluation must cover the same points of information the interrogator received from the senior interrogator. The interrogator submits the results of his evaluation to the senior interrogator, who uses this evaluation to update information about the interpreter. This evaluation may also be used to develop training programs for interpreters. STRATEGIC INTERROGATIONS AND DEBRIEFINGS Strategic debriefing is questioning of individuals who are sources of information in a strategic or operational environment This is done to obtain usable information in response to command and national level intelligence needs. Strategic intelligence --
The objective of the strategic debriefing process is to obtain information of the highest degree of credibility to satisfy outstanding information objectives (IO). This avoids surprises of a strategic nature and consequences. The types of sources encountered in strategic debriefing are emigres, refugees, resettlers, defectors, and selected US personnel. While there are other types, these represent the majority. Strategic debriefing guidance is provided in DIAM 58-13 and FM 34-5 S), Chapter 4. DUTIES AND RESPONSIBILITIES OF DEBRIEFERS Specific duties and responsibilities peculiar to a particular operation will be detailed in unit SOPs. This is due to the diverse nature of the various operations using debriefers outside continental United States (OCONUS) and within the continental United States (CONUS). However, debriefers have the following common duties and responsibilities regardless of assignment. Proper response to notification of the availability of a source will depend upon unit operations. The debriefer may have to respond spontaneously as in the case of walk-in sources. He may have the luxury of advance notice as in the case of an invitational interview. The process for planning a strategic debriefing is similar to conducting a tactical interrogation, with the following considerations peculiar to the strategic environment. The debriefer should --
The debriefer will usually use a friendly rapport posture with sources, who have a status far different from EPWs or detainees. Good questioning techniques, rapport, and effective lead follow-up ensure answering specific IO. Reporting Information Obtained Comprehensive and logical note taking is translated into objective reporting within the parameters of intelligence report procedures in DIAM 58-13. An interview is concluded in a manner which enables any debriefer to contact a source at a later date and resume the debriefing process. The debriefer ensures the source receives all promised incentives. It is often necessary to provide source transportation and lodging. Such considerations demand the debriefer be familiar with procedures for using Intelligence Contingency Funds (ICFs). There is an obvious need for OPSEC before, during, and after any debriefing. Source confidentiality and handling of classified materials demand constant and special attention. Maintaining a language proficiency is a basic requirement; improvement of dialects, slang, technical terminology, and military vocabulary is a must. A debriefer may have the added responsibility of maintaining local liaison with host-government agencies while OCONUS. Unit SOPs usually dictate necessary and proper procedures. The debriefer keeps abreast with target country S&T developments. Intelligence agencies publish numerous reports and summaries which are readily available to the strategic debriefer. STRATEGIC INTELLIGENCE COMPONENTS Information gathered as strategic intelligence may he categorized into eight components. An easy way to remember these components is the acronym "BEST MAPS":
Each of these components can be divided into subcomponents. These components and subcomponents are not all-encompassing nor mutually exclusive. This approach enhances familiarization with the types of information included in strategic intelligence. Biographic intelligence is the study of individuals of actual or potential importance through knowledge of their personalities and backgrounds. This component can be divided into subcomponents:
Biographic information is reported by a message intelligence report in accordance with the format in DIAM 58-13. Economic intelligence studies economic strength and weaknesses of a country. Its subcomponents are --
Sociological intelligence deals with people, customs, behaviors, and institutions. The subcomponents are --
Transportation and Telecommunications Intelligence Transportation and telecommunications intelligence studies systems dedicated to and used during military emergencies and peacetime. The subcomponents are too varied and numerous to cover. Military Geographic Intelligence Military geographic intelligence studies all geographic factors (physical and cultural) which may impact on military operations. Physical geography is concerned with natural or manmade geophysical features. Cultural geography provides demographics information. Armed forces intelligence is the integrated study of the ground, sea, and air forces of the country. This is often referred to as OB. It is concerned with --
Political intelligence studies all political aspects which may affect military operations. Its subcomponents are --
S&T intelligence studies the country's potential and capability to support objectives through development of new processes, equipment, and weapons systems. The subcomponents are --
Equally important to strategic intelligence components is awareness of the strategic intelligence cycle, and the debriefer's role within that 5-step cycle. The debriefers --
These evaluations measure information and report writing quality (see Appendix E). Evaluations provide vital feedback and guidance to strategic debriefers. Appendix F contains information on the command language program (CLP) and Appendix G, on individual and collective training.
|
|||||||||||||||||||||