|
Site Map FM 34-52 INTELLIGENCE INTERROGATION -- SEPTEMBER 28, 1992 |
|
CHAPTER 4:
PROCESSING AND EXPLOITING CAPTURED ENEMY DOCUMENTS STANAG 2084 defines a document as any piece of recorded information, regardless of form, obtained from the enemy, which subsequently comes into the hands of a friendly force. CEDs can be US or allied documents that were once in the hands of the enemy. CEDs are --
CEDs are mainly acquired two ways: Some are taken from sources; most, however, are captured on the battlefield from former enemy locations and enemy dead. Documents found on EPWs or detainees or on the battlefield -- which can be exploited more efficiently when combined with interrogation -- are forwarded with the EPW or detainee to the next echelon in the evacuation channel. In exceptional cases, documents may be evacuated ahead of the EPW or detainee for advance study by intelligence agencies. A notation should be made on the prisoner's captive tag (Figure 3-6), or accompanying administrative papers, about the existence of such documents and their location if they become separated from the EPW or detainee. EPW or detainee interrogation has its disadvantages. The main disadvantage is prisoner-derived information usually has to be confirmed from other sources; for example, OB, CEDs, and other EPWs or detainees. A prisoner may lie to further his army's cause or to ingratiate himself with the interrogator, by telling him what the prisoner believes he wants to hear. A prisoner may lack the background knowledge needed to interpret what he has seen or to pass it on accurately. He may misunderstand or misinterpret the interrogator's question because of language barriers or fright. An EPW or detainee may have been misinformed or misled concerning the true situation for any number of reasons. This does not mean EPW or detainee interrogation is fruitless; however, it should not be considered absolutely reliable. In contrast, a CED is something which the enemy has written for its own use. For this reason, CEDs are usually truthful and accurate. Spectacular cases have occurred in which falsified documents have been permitted to fall into enemy hands as a means of deception. However, these cases are exceptions and thus are usually famous. Because deceptive documents are unusual, a commander tends to believe in the authenticity of captured documents. Information contained in CEDs can prove to be of intelligence value to commanders at all levels. CEDs are important because they provide information directly from the enemy. Only rarely will a single document or group of documents provide vital information. Usually, each document provides a small bit of a larger body of information. Each CED, much like a single piece of a puzzle, contributes to the whole. In addition to their tactical intelligence value, technical data and political indicators can be extracted from CEDs that are important to strategic and national level agencies. CEDs can be helpful in exploiting sources. The handling methods and reporting procedures to be used by US personnel acquiring CEDs are contained in STANAG 2084. It states CEDs, except those belonging to captured enemy equipment (CEE), will be forwarded for exploitation to the appropriate captured DOCEX center (normally organic to major North Atlantic Treaty Organization [NATO] commands). There are three types of documents:
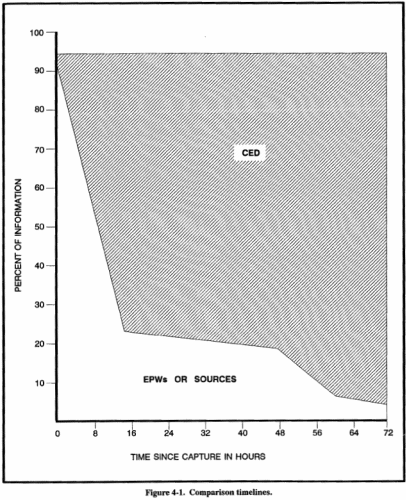
The volume of CEDs in combat will overwhelm an interrogation element of the size projected for a heavy division. A flow of CEDs similar to those encountered in OPERATIONS URGENT FURY, JUST CAUSE, and DESERT STORM would supply enough targets to keep a light division's interrogators busy around-the-clock screening and categorizing CEDs. Any attempt to conduct deeper exploitation would result in a tremendous evacuation delay and the end of timely reporting. Experience shows a division involved in a HIC may have to process between 525 and 5,300 sources per week. While these figures are estimates, they demonstrate the inability of a division's own interrogators to simultaneously exploit sources and CEDs. Divisions may receive additional interrogation assets from corps, depending on their mission. Prior planning must be conducted to establish the availability of these assets and their deployment within the division. The density of interrogation assets and command emphasis on the collection effort determine mission requirements. The feasibility of a dual collection mission may also be the result of initial IPB by the commander's intelligence staff. If an echelon cannot conduct a dual collection effort, EPW interrogation receives priority. CEDs, while not affected by memory loss, are often time sensitive; therefore, they are quickly screened for possible exploitation. Interrogators are given the CED exploitation mission because of their linguistic ability. This makes printed and typed material readily exploitable, but many handwritten documents are illegible. Information contained in undeveloped imagery and recordings is inaccessible to most interrogation elements. The intelligence value of painted, drawn, or engraved material cannot be exploited by many elements unless it is accomplished by explanatory information in writing. An example of this would be an overlay prepared without map data, registration points, or identifying terrain features. In spite of these limitations, an estimated 90 percent of all the information contained in CEDs can be exploited. Figure 4-1 shows a comparison along a timeline of the amounts of information available to the interrogator from the two collection targets. The comparison assumes the CEDs and sources initially had the same amount of information, and it was of equal intelligence value. The figures used are conservative estimates, and the time between the two target types might be even greater between 24 and 72 hours. The percentage of information available from sources drops sharply during the first 24 hours after capture. This represents the rapid loss of what sources would consider to be insignificant details. A slower drop in the percentage begins at 48 hours to represent the resurgence of established value systems. This resurgence makes it harder for interrogators to obtain what information the source still remembers. The category assigned to each CED must be recorded as part of the captured Document Log entry for that CED. Interrogators should also enter a brief description of that CED. This description should identify the type of document (such as sound recording, written material, painting, engraving, imagery); and what language was used in the CED. This entry should also specify the physical construction of the CED (such as typed, printed, handwritten, tape cassette, photographs, film) and give some indication of its size (such as the number of pages, rolls of film, cassettes). The categories are discussed below. CATEGORY A Category A documents --
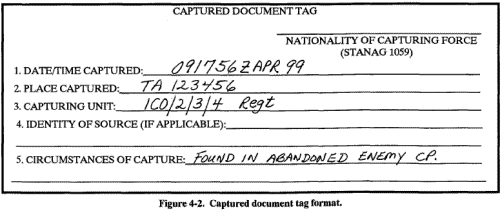
Significant intelligence topics include enemy OB, new weapons or equipment on the battlefield, and may contain information that indicates a significant change in the enemy's capabilities or intentions. When a document is identified as Category A, the document examiner immediately ceases screening operations and submits a spot report in SALUTE format of the critical information from the document. The examiner then resumes screening operations. CATEGORY B Category B documents contain information pertaining to enemy cryptographic or communication systems. Once a document is identified as category B, it is classified SECRET. This is done to limit the number of people having knowledge of the capture or contents. Figure 4-1. Comparison timelines. Category B documents may contain spot reportable information, thereby requiring immediate exploitation. In every case, these documents will be transferred through secure channels to the technical control and analysis element (TCAE) or TSA as soon as possible. CATEGORY C Category C documents contain no spot reportable or time-sensitive information, but do contain information of general intelligence value that does not indicate significant changes in enemy capabilities or intentions. Category C documents may be of interest or value to other agencies. When identified as Category C, they require exploitation, regardless of content. Category D documents appear to contain information of no intelligence value. Documents are not identified as Category D until after a thorough examination by document translation specialists at the highest command interested. This is accomplished at EAC. Category D documents are to be disposed of as directed by the appropriate authority. The accountability phase begins at the time the document is captured. Original documents must not be marked, altered, or defaced in any way. Documents must be clearly tagged. The capturing unit attaches a captured document tag (DA Form 5976, Part C) to each document; multiple CEDs are bundled or bagged together. The capture data is always recorded on a captured document tag. Figure 4-2 shows a format to use when a capture tag is not available; record the required data on any paper. The captured document tag should be assigned a sequential number at the first formal exploitation point, showing the nationality of the capturing force by national letters prescribed in STANAG 1059. The capturing unit will record the information as follows:
CED intelligence value will be determined and exploited as early as possible. The document must be forwarded immediately to higher headquarters. 4-2. Captured document tag format. Custody of CEDs transfers (normally from the MP) to MI when MI identifies a document as having intelligence interest. When MI interest in an EPW-related CED stops, MI gives it back to the MP. There is no set time for how long any particular echelon may keep a document for study. The primary aim of speedy evacuation to the rear for interrogator examination remains. During evacuation, escorts carefully guard CEDs to prevent recapture, loss, or destruction. Capturing Unit Responsibilities The capturing unit is responsible for properly tagging and securing CEDs found on an EPW or on the battlefield. It forwards CEDs found on the battlefield directly to its S2. Documents found on an EPW stay with him. If the capturing unit takes CEDs from a captured person, it does so in accordance with the GPW and unit SOPs. The capturing unit must clearly tag CEDs to show which EPW it was taken from so they can be matched up later. Specific responsibilities are discussed below. Capture Unit's S2. This officer is responsible for tagging all untagged CEDs. The S2 performs battlefield DOCEX as practicable and ensures speedy CED evacuation to brigade. Escort or Guards. Brigade and Below. The brigade provides escorts and guards to transport EPWs and CEDs from subordinate battalions to the division forward collecting point. The guards --
Brigade IPW Team. This 2- to 4-person team's mission, when placed in DS, is to collect information of critical interest to the supported brigade commander. It concentrates whatever DOCEX efforts it can on CEDs found with EPWs. MP evacuate all examined CEDs, along with unexamined CEDs, via EPW evacuation channels. Division IPW Section. This interrogation section's mission is similar to that of the brigade IPW team. At this stage, priority evacuation of high value EPWs and CEDs direct to EAC is possible. Most EPWs and CEDs of intelligence interest go to the corps EPW holding facility. MP Escorts. MP assume responsibility for evacuating CEDs and EPWs from the brigade's capturing units at the division's forward collecting point. They escort EPWs and CEDs through EAC. MI assumes control from the MP when interrogators determine a captured item or EPW is of intelligence value. Corps CED Team. The CIF commander may task-organize a team of interrogators at the corps EPW holding facility to screen incoming CEDs for examination by the CIF DOCEX element. The CED screening team --
CIF DOCEX Element. At the CIF or combined corps interrogation facility (CCIF), interrogators scan selected CEDs and decide their intelligence category. They assign serial numbers and examine CEDs to answer corps collection requirements, filing spot reports in SALUTE format as necessary. CIF interrogators batch and forward Category B documents to specialized collection activities. Interrogators label, batch, and direct evacuation of all other documents to EAC via MP and EPW evacuation channels. Examples are the TECHlNT team, CI team for espionage items, and Criminal Investigation Division (CID) or SJA for war crimes information. Theater Document Examiners. Theater level interrogators, normally at a TIF, perform a final examination of all documents of possible theater intelligence value before storing or evacuating them. The Defense Intelligence Agency (DIA) sets procedures for exploitation of documents above theater Army level. The following procedures have been devised to aid timely exploitation:
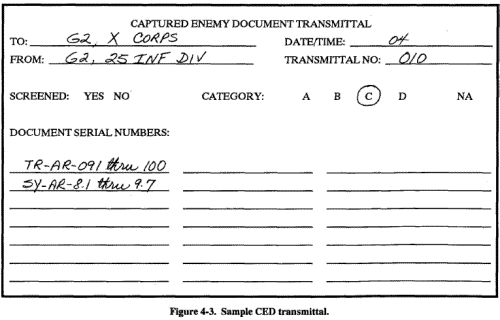
At each echelon, starting with the capturing unit, steps are taken to ensure CED accountability is maintained during document evacuation. To establish accountability, the responsible element inventories all incoming CEDs. Thorough accountability procedures at each echelon ensure CEDs are not lost. To record each processing step as it occurs helps correct mistakes in CED processing. Accountability is accomplished by anyone who captures, evacuates, processes, or handles CEDs. All CEDs should have completed captured document tags. An incoming batch of documents includes a CED transmittal. Figure 4-3 shows this format. The exact format for a document transmittal is a matter of local SOP, but it should contain the information listed below:
When a batch is received without a transmittal, the interrogation element contacts the forwarding unit and obtains a list of document serial numbers. The interrogation element records all trace actions in its journal. Accountability includes --
Figure 4-3. Sample CED transmittal. When intelligence derived from a CED is included in a unit or information INTREPs, the identification letters and number of the document concerned are quoted to avoid false confirmation. All CEDs are shipped with any associated documents. An inventory of incoming CEDs is conducted initially by comparing the CED to the captured document tag and accompanying transmittal documents. This comparison identifies --
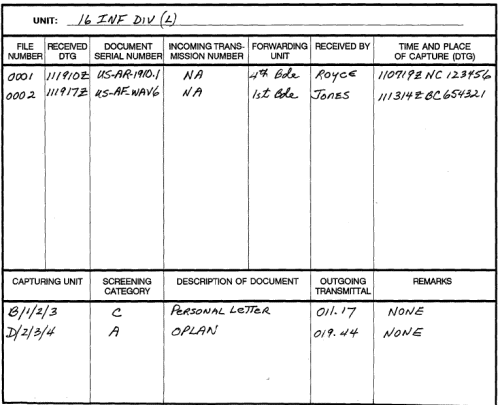
The captured document log, shown at Figure 4-4, is a record of what an element knows about a CED. After trace actions are initiated, the CEDs are entered in the remarks section of the captured document log. This log must contain the following:
Accountability for the CED should be established at each echelon once the actions described above have been done. When necessary, the receiving unit initiates a CED trace action. Trace actions are initiated on all missing CEDs, captured document tags, and all information missing from the captured document tag. Trace actions are initiated by contacting elements from which the documents were received. This corrective action can be completed swiftly if that unit's captured document log was filled out completely. If necessary, the trace action continues to other elements that have handled the document. If a captured document tag is unavailable from elements that have previously handled the CEO, the document examiner fills out a captured document tag for the document using whatever information is available. Attempts to obtain missing CEOs are critical because of the information those CEDs might contain. As incoming CEDs are accounted for, the exploitation phase for intelligence information begins. Exploitation includes --
Figure 4-4. Captured document log format. CEDs are processed and exploited as soon as possible within the constraints of the unit's mission. The main mission of some units is to exploit human sources rather than to translate CEDs; therefore, manpower constraints may limit time for translation. However, translating CEDs is necessary at any echelon where interrogators and translators are assigned. Therefore, it is important that interrogation elements possess qualified personnel to provide the translation support required. Intelligence units ensure there is no delay in CED exploitation. Qualified personnel or document copying facilities should be available to handle CEDs; personnel should be available to exploit the volume or type of documents concerned. If not, documents are forwarded immediately to the next higher echelon. Copying availability is determined by the echelon in question, as well as mission and mobility considerations. Document exploitation begins when CEDs are screened for information of immediate intelligence interest. As each document is screened, it is assigned one of four category designations. The category assigned determines the document's priority for exploitation and evacuation. CED screening procedures include receiving the latest PIR, JR, and SIR; current friendly and enemy situation update; relevant OB; and review. Brigade and division interrogators get this information from the supported J2, G2, or S2. Corps and theater DOCEX elements receive this information from their parent MJ battalion or brigade. The DOCEX elements are responsible for obtaining and providing such operational intelligence information to their DOCEX teams. TECHDOCs are given special handling to expedite exploitation and evacuation. TECHDOCs are handled as category A CEDs until screened by TECHINT personnel. Generally, TECHDOCs accompany the captured equipment until the intelligence exploitation is completed. TECHDOCs include maintenance handbooks, operational manuals, and drawings. Examples of TECHDOCs include --
CEDs can be recategorized during screening conducted at higher echelons. The information may have become outdated, or the echelon currently exploiting the document may have different intelligence requirements. Once a CED has been screened, the document must be exploited. The translation must be clearly and accurately typed or handwritten; this ensures usability. Also, as part of interrogation duties, the interrogator may have previously translated a document by sight to help gain a source's cooperation. There are three types of translations:
A summary translation requires a translator have more analytical abilities. The translator must balance the need for complete exploitation of the document against time available in combat operations. A summary translation may also be used by translators working in languages in which they have not been formally trained. For instance, a Russian linguist may not be able to accurately deliver a full translation of a Bulgarian language document. However, he can probably render a usable summary of the information it contains. Except for SALUTE spot reports, all information resulting from document exploitation activities will be reported in a translation report. After all required SALUTE reports have been submitted, the translator will prepare required translation reports. CEDs that contain information of intelligence value that was not SALUTE reported are the subject of translation reports. Translation reports are prepared on all Category C CEDs and include portions of Category A, TECHDOCs, and Category B CEDs not SALUTE reported. The priorities for preparing translation reports are --
A translation report, shown at Figure 4-5, should contain the following information:
The translator records each exploitation step taken in the captured document log. Transmission of spot and translation reports is entered in the element's journal. At least two copies are prepared for each spot (SALUTE) and translation report. One copy is placed in the interrogation elements's files. The other accompanies the CED when it is evacuated. When the CED cannot be fully exploited, a copy of the CED should be made and retained. The original CED is forwarded through evacuation channels. Even when copies of an unexploited CED cannot be made, the original CED is still forwarded through evacuation channels without delay. Figure 4-5. Sample translation report. For friendly forces to benefit fully from a document, send CEDs to the element most qualified to exploit them as quickly as possible. Information gained from a CED is frequently time-sensitive. If a document is not sent to the element most capable of exploiting it, time will be lost. Time lost in exploiting the document may reduce or even negate the value of the information. The CED evacuation procedures in use at any element must ensure documents are shipped to their proper destinations in a timely manner. CEDs are normally evacuated from echelon to echelon through the intelligence organizational chain. Depending on the type of documents, they may eventually be evacuated to the National Center for Document Exploitation. Interrogators and translators can exploit CEDs at every echelon; they will make an attempt to exploit CEDs within their expertise and technical support constraints. Some CEDs are evacuated to different elements based upon the information contained and the type of document concerned. Direct evacuation to an element outside the chain of command takes place at the lowest practical echelon. Specific evacuation guidelines contained in local unit SOPs are followed when dealing with documents requiring special handling. When transportation assets are limited, CEDs are evacuated according to priority. The priority is the category assigned to the CED. All Category A CEDs will be evacuated first, TECHDOCs will be considered Category A CEDs until examined by the captured materiel exploitation center (CMEC), followed in order by Categories B, C, and D. Category B documents are evacuated to the TCAE, which maintains a SIGINT and EW data base. Category B documents pertaining to communications equipment are duplicated, if possible; the duplicate documents are sent to the CMEC. CEDs not evacuated are held until the next transportation arrives. These remaining CEDs are combined with any other CEDs of the same category that have arrived and have been processed. When determining evacuation priorities, interrogators consider CEDs ready for evacuation. Lower priority CEDs, no matter how old, are never evacuated ahead of those with higher priority. A package of documents contains CEDs of only one category. All unscreened CEDs are handled as Category C documents, but they are not packaged with screened Category C documents. CEDs in a single package must have the same destination. When CEDs are evacuated from any echelon, a document transmittal is used (see Figure 4-3). A separate document transmittal is prepared for each group of CEDs to be evacuated. When second copies of Category B CEDs are being sent to a TECHINT element, a separate document transmittal is required. The transmittal identification number is recorded in the captured document log as part of the entry for each CED. All CEDs being evacuated must be accompanied with the appropriate --
Preparations for further CED evacuation begin with verifying document serial numbers. This is done by comparing the entry in the captured document log with the entry on the captured document tag attached to each CED. Once all CEDs are present, copies of all reports derived from the CEDs are assembled. A copy of all SALUTE and translation reports is placed with the CEDs that were the sources of those reports. When possible, all Category B CEDs and their captured document tags should be copied. CEDs are first grouped according to their assigned screening category. Personnel must be careful when sorting CEDs to ensure no CED is separated from its associated documents. These large groupings can be broken down into smaller groups. Each of these smaller groupings consists of CEDs that were --
DOCUMENTS CAPTURED WITH A SOURCE The documents captured with a source play an important role in the interrogation process and can contain reportable information the same as with a CED obtained on the battlefield. During source screening operations, for instance, documents can indicate a specific source may have information pertaining to the commander's intelligence requirements. The interrogator uses various pieces of information in forming his interrogation plan. Documents captured with the source may provide the key to the approach necessary to gain the source's cooperation. Guidelines for the disposition of the source's documents and valuables are set by international agreement and discussed in more detail in AR 190-8 and FM 19-4. One way the source's trust and continued cooperation can be gained is through fair and equitable handling of his personal possessions. In some instances, such treatment can make it more likely the source will cooperate during interrogation. Furthermore, fair treatment by the interrogator and holding area personnel can ease tensions in the confinement facility. The disposition of documents captured with a source is normally an MP function. Because of their language capabilities, interrogators at the compound probably will be required to provide assistance. The MP sign for all documents taken from sources. To ensure proper handling and expeditious disposition of these documents, the interrogation element should sign for any documents captured with a source. When the interrogation element assumes control of documents, they process them according to established procedures. When documents are captured with a source, it is recommended that they be taken away from him so he cannot destroy them. However, under no circumstances is a source's identification card to be permanently taken from him. When documents are taken from a source, it is necessary to ensure the source from whom they were taken can be identified. The best way to do this is with the source's captive tag. The bottom portion of the tag is designed to be used for marking equipment or documents. Three possible actions may be taken with documents captured with a source. The documents may be confiscated, impounded, or returned to the source. Documents confiscated from a source are taken away with no intention of returning them. Official documents, except identification documents, are confiscated and appropriately evacuated. The intelligence value of the document should be weighed against the document's support in the interrogation of the source. Category A documents require exploitation and should be copied. One copy should be translated and exploited separately, and the other copy should be evacuated with the source. If copying facilities are not available, a decision should be made on whether to evacuate the document with the source or separately. Category B CEDs should be evacuated to the TCAE for appropriate exploitation. Category C official documents can best be used in the interrogation of the source. Therefore, these CEDs and Category D official documents should be evacuated with the source. Impounded CEDs are taken away with the intention of returning them later. When a document is impounded, the source must be given a receipt. The receipt must contain a list of the items impounded and the legible name, rank, and unit of the person issuing the receipt. All personal effects, including monies and other valuables, will be safeguarded. An inventory of personal effects that have been Impounded will be entered on DA Form 4237-R (see Figure 3-1). Also, the officer in charge or authorized representative will complete and sign DA Form 1132-R (Prisoner's Personal Property List - Personal). A copy will be provided the source. See AR 190-8 for procedures on handling personal effects. Returned CEDs are usually personal in nature, taken only for inspection and information of interest, and immediately given back to the source. Personal documents belonging to a source will be returned to the source after examination in accordance with the GPW. Copies of such papers may be made and forwarded if considered appropriate. An identification document must be returned to the source. RECOGNITION AND EVACUATION OF DOCUMENTS In a fast-moving tactical situation, it is possible documents captured with sources will not be handled expeditiously. Final disposition of these documents may not be made until the source is evacuated at least as far as the corps holding area. Some documents captured with a source will aid in the interrogation of the source. Others, particularly category A, should be copied and evacuated separately. One copy can remain with the source to aid in the interrogation, and the other can be translated and exploited separately. It is essential that the capturing unit correctly identify the documents captured with the source. This is more easily done when the interrogation element, rather than the MP element, signs for the documents captured with sources. EVACUATION Of SIGNIFICANT DOCUMENTS To efficiently exploit CEDs and sources, documents captured with a source are normally evacuated with the source. A document of great significance may be evacuated ahead of the source, but a reproduction should be kept with the source. If reproduction is not possible, note on the captured document tag where the document was sent. Significant documents such as categories A and B, TECHDOCs, maps, charts, AIRDOCs, and NAVDOCs are evacuated directly.
|