|
Site Map FM 34-52 INTELLIGENCE INTERROGATION -- SEPTEMBER 28, 1992 |
||
|
APPENDIX C:
S2 TACTICAL QUESTIONING GUIDE AND BATTLEFIELD EXPLOITATION
OF CAPTURED ENEMY DOCUMENTS AND EQUIPMENT History shows that EPWs, CEDs, and CEE are critical sources of combat intelligence. It has also shown the usefulness of information is directly proportionate to how fast a commander can get it. OPERATIONS URGENT FURY, JUST CAUSE, and DESERT STORM proved that without workable procedures to handle captured persons or items, our combat effectiveness suffers because the evacuation chain jams the forward resupply effort. We also suffer because we have not exploited combat information sources at a low enough echelon to do that commander any good. This guide is for battalion and brigade S2s. It explains standard procedures on what to do when the S2 --
PERSONNEL HANDLING There are two types of persons captured on the battlefield: combatants and noncombatants. PM 27-10 defines the two types. The capturing unit treats all combatants and noncombatants as EPWs until the division forward collecting point segregates them by category. This is whether they are soldiers, clergy, or medics (see Chapter 3). Noncombatants are handled, questioned, detained, evacuated, and released in accordance with theater policy. At the EPW's capture point, the capturing element performs the following steps, with the senior soldier responsible for ensuring they are done. The steps are referred to as the "five S's." STEP 1. SEARCH The POC unit's first job is to disarm, then search all EPW or detainees, and tie their hands behind their back. They gather all loose enemy documents and equipment in the area. They evacuate them with the EPW. Documents and personal and protective military equipment stay with the prisoner unless otherwise directed by the battalion S2. STEP 2. SILENT The capturing unit instructs or signals EPWs to be silent. If that does not work, the EPW is gagged. Guards give orders to EPWs, but do not talk nor give them comfort items. STEP 3. SAFEGUARD The POC unit immediately moves the EPWs out of the fire zone. They protect EPWs from reprisals and give them medical care as necessary. The POC unit tries to preserve the shock of capture until brigade interrogators have a chance to question the EPWs. STEP 4. SEGREGATE The POC unit orders the EPWs to sit on the ground. It separates officers from enlisted, senior from junior, male from female, and civilian from soldier. It prepares a captive tag and puts one on each EPW (Figure 3-4). Tagging procedures are discussed under equipment handling procedures below. STEP 5. SPEED TO THE REAR Lastly, the POC unit moves EPWs to the unit supply point for evacuation. All captured documents, personal effects, and portable enemy equipment go with the EPW. Also, one escort guard should know the EPW's circumstances of capture. CAPTURED ENEMY DOCUMENTS FOUND ON ENEMY PRISONER OF WAR The battalion S2, and subordinate unit commander, ensures CEOs found on EPWs are handled as follows. The POC unit will --
CAPTURED ENEMY DOCUMENTS FOUND ON THE BATTLEFIELD An example of CEDs found on the battlefield is paperwork discovered in an overrun CP, but not on an EPW's person. The POC unit will --
EQUIPMENT HANDLING PROCEDURES CEE includes all types of foreign materiel found on an EPW or on the battlefield that may have military application. The POC unit --
ITEMS OF TECHINT VALUE The capturing unit may recognize certain CEE as having possible TECHINT value. Such items include --
The capturing unit's primary job when capturing a TECHINT item is to secure and report the capture to its S2 for disposition instructions. Figure C-1 provides a scenario for TECHINT items. FIRST ECHELON BATTLEFIELD TECHINT EXPLOITATION It is conceivable, although not likely, that the capturing unit leader or S2 may need to do field exploitation of a piece of CEE. If this happens --
TAGGING PROCEDURES There are two capture tags: A CEE tag and an EPW tag with a smaller tear-off document tag. The POC unit tags all captured personnel, CEDs, and CEE at the POC. The battalion S2 or company commander is responsible for having sufficient CEE and EPW document tags as well as and waterproof bags prior to an operation. When no standard tag forms are available, the following procedures will be used for expediency:
TACTICAL QUESTIONING This section provides "how to" instructions to enable the S2 to do tactical questioning (TQ) on EPWs. Following these will --
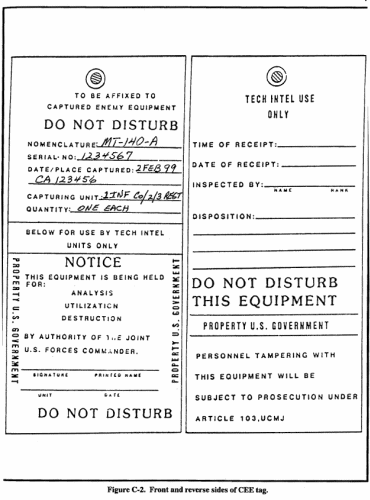
WARNING Improper, unlawful, or inept attempt at field exploitation can harm or destroy possible critical intelligence sources, and send US soldiers to prison. Any decision to attempt these procedures is a command responsibility, and only done by the S2. Figure C2 is an example of the front and reverse sides of a CEE tag. It should be included as a tab to the TECHINT appendix in the Intelligence annex of an OPLAN plan or operations order (OPORD). The purpose of TQ is to obtain combat information of immediate use to the battalion or subordinate unit by the S2. Sources of information can be an EPW and local or friendly civilians encountered in the operational area. (S2s use established procedures when questioning local or friendly civilians.) LANGUAGE REQUIREMENT TQ can be done only under one of following circumstances:
WHERE TQ IS DONE TQ is done as soon as possible after removing the EPW from fire zones. However, battalion or brigade commanders forced to deal with heavy EPW input may set up an organized TQ effort at the unit's EPW collecting point. WHO ASKS THE QUESTIONS Only the S2 is authorized to conduct TQ. The S2 asks every question himself, even when using another soldier or local national as an interpreter. If augmented by interrogators, the interrogation team supervises the TQ effort. TIME CONSIDERATIONS TQ is designed to be a quick procedure, lasting from 5 to 20 minutes. A command decision is required if source questioning interferes with mission accomplishment or delays a priority evacuation. ITEMS NEEDED FOR TQ TQ is authorized for collection of combat information critical to successful mission accomplishment. The questioner needs to know what information headquarters requires. Other items required for TQ are --
THE EXPLOITATION PROCESS The exploitation process, discussed in Chapter 3, is the basis for all personnel examinations, to include TQ. It consists of three parts: screening, questioning, and reporting. Figure C-2. Front and Reverse sides of CEE tag. SCREENING If there is more than one EPW, the quickest method to pick who to question first is to --
QUESTIONING The key to questioning is brevity. Tactical questioners work fast until they find an EPW who will give useful combat information. To do this, the tactical questioner --
REPORTING Tactical questioners report acquired information in SALUTE format (Figure 3-5). To do this, they --
THE TACTICAL QUESTIONING PLAN The questioning plan used during TQ is short, simple, and standard. The questioner can use it to uncover spot reportable information on any subject. An easy way to remember it is through the phrase "BIG 4 and JUMP."
More specifically, the TQ plan covers the following topics in sequence. Figure C-3 shows examples of the BIG 4 and JUMP questions.
BATTLEFIELD DOCUMENT EXPLOITATION Battlefield DOCEX is a capturing unit procedure done by the S2 before interrogator exploitation. A combat unit without language-qualified personnel can perform limited battlefield DOCEX, mainly on maps and overlays. Units with linguists have the advantage of being able to do more.
Figure C-3. BIG 4 and JUMP question examples. After capturing an EPW or enemy CP, the capturing unit needs to look for maps, encrypted items, OPORDs, overlays, and other documents. The capturing unit then notifies headquarters to request disposition instructions. The small-unit leader safeguards the items pending disposition instructions. At the same time he --
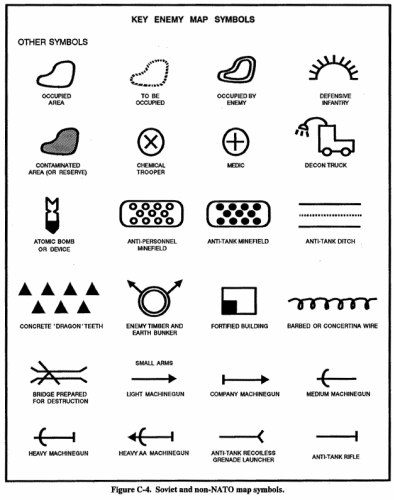
After finding information of possible value to the mission, the S2 extracts the combat information and uses the SALUTE format as a template to organize the information (see Figure 3-5). Figure C-4. Soviet and non-NATO map symbols.
|