|
Site Map FM 34-52 INTELLIGENCE INTERROGATION -- SEPTEMBER 28, 1992 |
||
|
CHAPTER 1:
MILITARY INTELLIGENCE MISSIONS AND INTELLIGENCE PREPARATION
OF THE BATTLEFIELD This manual is about interrogation operations. The purpose of this chapter is to define the interrogation mission and its critical elements; describe battlefield operations, IEW operations, and the intelligence processes, disciplines, and the mission, enemy, troops, terrain, and time available (METT-T) factors that shape and drive the interrogation process. It also addresses the personal qualities and special areas of knowledge of the interrogator and the capabilities and limitations of interrogation. It includes information on the various levels of conflict, interrogation missions, intelligence preparation of the battlefield (IPB) and the intelligence cycle. The level of detail is structured to assist you in understanding the interrogation tactics, techniques, and procedures described in the remainder of the manual. Battlefield operations demand seizing and maintaining the initiative. When operations are properly designed and executed, initiative accrues significant benefits from the outset of an operation to final victory. It permits attacking where, when, and what; while forcing the enemy to react and try to adapt to our operations. To gain the initiative, the commander must --
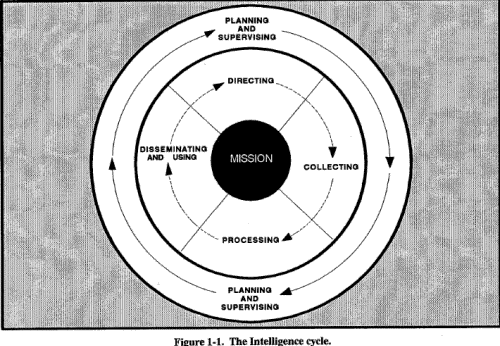
The commander uses defensive and offensive operations to destroy enemy first-echelon forces and deep-attack to simultaneously delay, disrupt, and manipulate enemy follow-on forces. The commander anticipates, creates, and exploits windows of opportunity, using flexible battle planning, to gain the initiative through offensive operations. By effectively employing maneuver and fire support assets, manipulating the enemy, and expertly using the weather and the terrain, the friendly commander can successfully defeat a superior enemy force. OPERATION DESERT STORM is an example of the successful application of this doctrine. IEW support is vital to the successful planning and execution of battlefield operations at all echelons. Intelligence support at brigade and battalion levels focuses primarily on close operations, while at division it focuses on close and deep operations. Corps is the focal point for intelligence operations that support rear and deep operations. Intelligence operations follow a four-phase process known as the intelligence cycle, which is shown at Figure 1-1. The intelligence cycle is oriented to the commander's mission. Supervising and planning are inherent in all phases of the cycle. Figure 1-1. The Intelligence cycle. The intelligence cycle is continuous. Although the four phases are conducted in sequence, all are conducted concurrently. While available information is processed and additional information is collected, the intelligence staff is planning and directing the collection effort to meet new demands. Previously collected and processed information (intelligence) is disseminated as soon as it is available or needed. The IEW system includes three MI disciplines: signals intelligence (SIGINT), imagery intelligence (IMINT), and HUMINT. Intelligence interrogation falls within the realm of HUMINT. SIGINT is derived from the intercept, analysis, and exploitation of threat communications and noncommunications radio- electronic emissions. IMINT is obtained from the analysis of radar, photographic, infrared, and electro-optical imagery. HUMINT is obtained from information collected from human sources and consists of the following intelligence collection operations:
After World War II, the US General Board on Intelligence surveyed 54 division G2s, 18 corps G2s, and 7 Army G2s. It concluded that 43 percent of all intelligence produced in the European theater of operations was from HUMINT, and 84 percent of the HUMINT was from interrogation. The majority of those surveyed agreed that interrogation was the most valuable of all collection operations. HUMINT is vital in all combat operations, regardless of echelon or intensity of conflict. By nature, HUMINT lends itself to the collection of information about the enemy's thought processes and intentions. HUMINT can provide information on almost any topic of intelligence interest, including order of battle (OB) factors, as well as scientific and technical (S&T) intelligence subjects. During OPERATION DESERT STORM, interrogators collected information which helped to --
INTELLIGENCE AND ELECTRONIC WARFARE OPERATIONS The intelligence cycle supports six tasks which are common to all echelons and which must be worked, at least in part, concurrently to satisfy the needs of the commander. The commander may have to prioritize these functions when resource and time constraints dictate. I&W identifies major shifts in enemy tactics, operations, and strategy which will set or change the terms of battle. They protect the commander from surprise and identify areas or times of risk by detecting enemy actions that are counter to planning assumptions.
I&W prevent surprise and minimize risk through the early identification of enemy activities and capabilities. INTELLIGENCE PREPARATION OF THE BATTLEFIELD IPB integrates the environment with the enemy's fighting doctrine and actions. It reveals his capabilities and vulnerabilities and allows the commander to systematically predict his actions. It also allows him to understand the battlefield and how to synchronize all of his battlefield operating systems for maximum effect. The results of IPE and staff wargaming are used to coordinate and synchronize the intelligence system regardless of the echelon at which it is performed or the intensity of conflict. IPB is more than preparation of the field of battle during hostilities. IPB considers the entire environment of conflict, supporting contingency as well as planning operations.
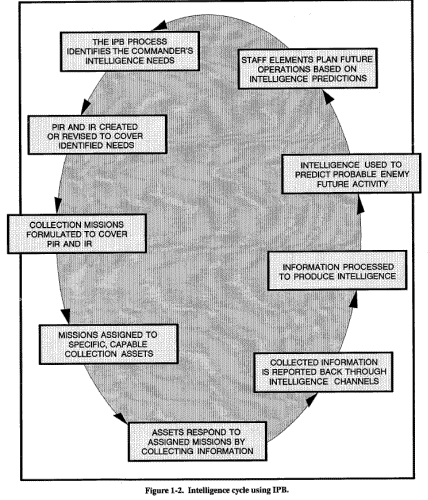
In mid-intensity conflict (MIC) to high-intensity conflict (HIC), IPB focuses on the traditional aspects of terrain, weather, and enemy. Many of the factors evaluated in IPB at the strategic level are used during IPB for low-intensity conflict (LIC) at the operational and tactical levels. Social, economic, and political factors that affect the environment of conflict are considered in IPB. The population must be examined in as much detail as the enemy and the terrain to understand what an enemy can or cannot do. Figure 1-2 shows the intelligence cycle using IPB.
Situation development confirms or denies the enemy COAs predicted in IPB. It confirms predicted centers of gravity and decisive points and identifies enemy strengths and vulnerabilities. This enables the commander to make timely decisions and effectively apply his combat power. TARGET DEVELOPMENT AND TARGET ACQUISITION Target development and target acquisition provide targets and targeting data for attacks by fire, maneuver, and electronic means. They identify and locate those targets that will have the greatest impact on the campaign's decisive engagements. These include deep operational reserves, strategic and operational level command, control, and communications (C3) nodes, key lines of communication, and air and naval staging facilities throughout the enemy's depth that contribute to his combat potential. At the tactical level, they address those HVTs that directly contribute to the application of combat power at decisive points on the battlefield. BATTLE DAMAGE ASSESSMENT (BOA) BDA provides the commander with the effect of friendly operations on the enemy. It focuses on the enemy's remaining military capabilities and potential. At the operational level, it also considers the campaign's effects on the enemy's economy and operational infrastructure as well as his military force structure. BDA is focused on providing effects of particular strikes and attacks, or a series of them. BDA is performed by the same collection assets used to satisfy the commander's intelligence and targeting priorities; therefore, BDA cannot be performed continuously without degradation of other capabilities, such as situation development and targeting. The commander must prioritize the BDA effort, identifying what he must know and when he must know it, just as he does for his PIR and targeting priorities. Force protection identifies friendly vulnerabilities and the enemy's efforts to exploit them. At the operational level, it includes the early identification of significant improvements in weapon lethality, the introduction of weapons of mass destruction into the conflict, or the commitment of terrorist or other unconventional forces into friendly rear areas. Force protection goes beyond countering enemy intelligence and includes the protection of all forces that contribute to our combat power. At the tactical level, it emphasizes measures to counter the enemy's intelligence collection capabilities and to protect the force from enemy action. MISSION, ENEMY, TROOPS, TERRAIN, AND TIME AVAILABLE FACTORS The METT-T factors are important to the commander when planning interrogation operations. METT-T determines how the commander will use interrogation assets. The effect of METT-T on interrogation missions is discussed below. The supported force's mission bears directly on how the interrogation element will be employed. In cordon and search operations, commanders may determine interrogators are best suited to screen the populace in order to identify insurgents and their supporters. In counter-drug operations, commanders may use interrogators to exploit documents and to train US and foreign agents in interrogation techniques. In all conflicts, the focus will be on EPW interrogation and CED exploitation. The mission influences interrogation operations in other ways. For example, if the force's mission is offensive, interrogation elements must be highly mobile, with secure communications to the supported G2 or S2. They must be constantly prepared to move forward with the element they are supporting. This limits time available for exploitation and dissemination. On the other hand, if the mission is defensive, interrogation elements have more time to exploit individual sources. They may also have more flexibility to exploit EPWs or detainees and CEDs, to fulfill the commander's intent to construct operational graphics. Collection requirements vary according to echelon. Strategic echelon requirements reflect the wide scope of interest of the theater and national command authority (NCA); whereas, tactical PIR and IR -- and resultant SIR -- reflect the immediate, more narrowly focused intelligence interest of the maneuver commander. The enemy, and our knowledge of the enemy, can influence interrogator assignments and the complexity of the exploitation process. One factor which affects interrogation operations is the type of opposing enemy force. The techniques and procedures used to collect from insurgents in a LIC may differ from those used to collect from regular enemy forces in a MIC to HIC. For example, an EPW from a regular forces unit may have undergone political indoctrination, but his commitment to his unit may not be as strong as that of the insurgent who is passionately committed to an ideal. Thus, interrogators may have more difficulty persuading the insurgent to talk. Another factor affecting interrogation operations is our current intelligence holdings on the enemy force and the interrogator's understanding of the threat. Our intelligence holdings on the composition of a newly formed insurgent organization usually will not be as complete as holdings on the composition of a regular enemy force. Thus, the focus of interrogation efforts in the early stages of a LIC may be on enemy force composition; whereas, the focus in a MIC or HIC may be on enemy force missions or intentions. Cultural aspects also affect interrogation missions. The employment of some basic interrogation techniques will differ based on the ethnic and cultural background of the enemy, and our failure to understand and adapt to this could hamper the collection effort. The number, experience level, and language proficiency of interrogators affect the tactical employment of interrogation elements. Due to the limited number of interrogators at any echelon, interrogation element commanders have to pick from available interrogators. They must manage personnel to ensure the most experienced are used to the best advantage (for example, to exploit complex enemy documents) and select EPWs most likely to answer SIR. Interrogation element commanders often have to contend with a mismatch between language-qualified personnel assigned to the unit and languages needed to perform the mission. They overcome the mismatch by acquiring local national (LN) interpreter support through the Assistant Chief of Staff, G1 (Personnel). They can also augment their interrogators by requesting other available linguists within the supported command to serve as interpreters. Another troop-related factor which affects interrogation operations is the training of all soldiers on EPW handling and evacuation. EPW treatment during the early stages of capture is critical to the success of subsequent interrogations. The availability of military police (MP) support at brigade and above can enhance interrogation activities. Interrogation operations are more effective in a controlled environment where EPWs are adequately guarded. Terrain and weather are relevant to interrogator operations and affect site deployments, communications, and mobility. MP must ensure proper shelter and security for the EPW facility if it is collocated or immediately adjacent to the EPW collecting point or internment facility. Information collected through interrogation operations is valuable only if it is reported in a timely manner. Exploitation procedures may need to be adjusted to make the most use of time available. At the tactical level, interrogations will be brief, PIR driven, and reported in concise formats such as size, activity, location, unit, time, equipment (SALUTE). At the operational and strategic levels, time will generally allow for a more expanded interrogation effort and flexible reporting format, such as the intelligence information report (IIR). The challenge is for interrogators to be proficient linguists and skilled members of a highly organized collection activity. This ensures the acquisition of the maximum amount of pertinent information regardless of time available. Like other intelligence assets, interrogators must serve the commander. Interrogation operations are of no value unless they contribute to the accomplishment of the supported commander's mission. To understand the interrogator's role in mission accomplishment, one must understand the interrogation process. Interrogation is the process of questioning a source to obtain the maximum amount of usable information. The goal of any interrogation is to obtain reliable information in a lawful manner, in a minimum amount of time, and to satisfy intelligence requirements of any echelon of command. Sources may be --
A good interrogation produces needed information which is timely, complete, clear, and accurate. An interrogation involves the interaction of two personalities -- the source and interrogator. Each contact between these two may differ because of individual characteristics and capabilities of the participants. Furthermore, the circumstances of each contact and physical environment vary. Other forms of intelligence interrogations include interviews, debriefings, and elicitations. There are certain principles which generally apply to all types of interrogations; namely, the objective, the prohibition against use of force, and security. Each interrogation must be conducted for a definite purpose. The interrogator must keep this purpose firmly in mind as he proceeds to obtain usable information to satisfy the assigned requirement, and thus contribute to the success of the unit's mission. The objective may be specific -- establish the exact location of an ammunition storage facility. Or it may be general -- seek to obtain OB information about a specific echelon of the enemy forces. In either case, the interrogator must use the objective as a basis for planning and conducting the interrogation. He should attempt to prevent the source from becoming aware of the true objective of the interrogation. The interrogator should not concentrate on the objective to the extent he overlooks or fails to recognize and exploit other valuable information extracted from the source. For example, during an interrogation, the interrogator learns of the presence of a heretofore unknown, highly destructive weapon. Although this information may not be in line with his specific objective, the interrogator must develop this important lead to obtain all possible information concerning this weapon. It becomes obvious an interrogation objective can be changed as necessary or desired. PROHIBITION AGAINST USE OF FORCE The Intelligence Staff Officer (J2, G2, or S2) has responsibility for all command intelligence functions. He assists the commander by --
One of the significant means used by the intelligence staff is the interrogation of the following:
These persons are protected by the Geneva Conventions for the Protection of War Victims of August 12, 1949, as they relate to captured wounded and sick enemy personnel (GWS), retained enemy medical personnel and chaplains (GWS), enemy prisoners of war (GPW), and civilian internees (GC). Captured insurgents and other detained personnel whose status is not clear, such as suspected terrorists, are entitled to PW protection until their precise status has been determined by competent authority. In conducting intelligence interrogations, the J2, G2, or S2 has primary staff responsibility to ensure these activities are performed in accordance with the GWS, GPW, and GC, as well as US policies, regarding the treatment and handling of the above-mentioned persons. The GWS, GPW, GC, and US policy expressly prohibit acts of violence or intimidation, including physical or mental torture, threats, insults, or exposure to inhumane treatment as a means of or aid to interrogation. Such illegal acts are not authorized and will not be condoned by the US Army. Acts in violation of these prohibitions are criminal acts punishable under the UCMJ. If there is doubt as to the legality of a proposed form of interrogation not specifically authorized in this manual, the advice of the command judge advocate should be sought before using the method in question. Experience indicates that the use of prohibited techniques is not necessary to gain the cooperation of interrogation sources. Use of torture and other illegal methods is a poor technique that yields unreliable results, may damage subsequent collection efforts, and can induce the source to say what he thinks the interrogator wants to hear. Revelation of use of torture by US personnel will bring discredit upon the US and its armed forces while undermining domestic and international support for the war effort. It also may place US and allied personnel in enemy hands at a greater risk of abuse by their captors. Conversely, knowing the enemy has abused US and allied PWs does not justify using methods of interrogation specifically prohibited by the GWS, GPW, or GC, and US policy. Limitations on the use of methods identified herein as expressly prohibited should not be confused with psychological ploys, verbal trickery, or other nonviolent or noncoercive ruses used by the interrogator in the successful interrogation of hesitant or uncooperative sources. The psychological techniques and principles in this manual should neither be confused with, nor construed to be synonymous with, unauthorized techniques such as brainwashing, physical or mental torture, or any other form of mental coercion to include drugs that may induce lasting and permanent mental alteration and damage. Physical or mental torture and coercion revolve around eliminating the source's free will, and are expressly prohibited by GWS, Article 13; GPW, Articles 13 and 17; and GC, Articles 31 and 32. Torture is defined as the infliction of intense pain to body or mind to extract a confession or information, or for sadistic pleasure. Examples of physical torture include --
Examples of mental torture include --
Coercion is defined as actions designed to unlawfully induce another to compel an act against one's will. Examples of coercion include --
Specific acts committed by US Army personnel may subject them to prosecution under one or more of the following punitive articles of the UCMJ:
See Appendix A for the text of these offenses. While using legitimate interrogation techniques, certain applications of approaches and techniques may approach the line between lawful actions and unlawful actions. It may often be difficult to determine where lawful actions end and unlawful actions begin. In attempting to determine if a contemplated approach or technique would be considered unlawful, consider these two tests:
If you answer yes to either of these tests, do not engage in the contemplated action. If a doubt still remains as to the legality of a proposed action, seek a legal opinion from your servicing judge advocate. The approaches, psychological techniques, and other principles presented in this manual must be read in light of the requirements of international and US law as discussed above. Authority for conducting interrogations of personnel detained by military forces rests primarily upon the traditional concept that the commander may use all available resources and lawful means to accomplish his mission and to protect and secure his unit. It is the stated policy of the US Army that military operations will be conducted in accordance with the law of war obligations of the US. The GWS, GPW, and GC establish specific standards for humane care and treatment of enemy personnel captured, retained, or detained by US military forces and its allies. Suspected or alleged violations of these standards will be reported, investigated and, if appropriate, referred to competent authority for trial or other disposition. Violations of the GWS, GPW, or GC committed by US personnel normally constitute violations of the UCMJ. The commander is responsible for ensuring that the forces under his command comply with the GWS, GPW, and GC. Should violations occur in the conduct of warfare, the commander bears primary responsibility for investigating and prosecuting violations. The interrogator, by virtue of his position, possesses a great deal of classified information. He is aware his job is to obtain information, not impart it to the source. He safeguards military information as well as the source of that information. This becomes very clear when one considers that among those persons with whom the interrogator has contact, there are those attempting to collect information for the enemy. The interrogator is alert to detect any attempt made by the source to elicit information. DEFINITION OF PRISONER OF WAR AND ENEMY PRISONER OF WAR A PW is a US or allied person detained by an enemy power. An EPW is a person detained by US or allied powers. The first issue interrogators must deal with is who must be afforded PW treatment. Figure 1-3 paraphrases Article 4 of the GPW. In addition, the following personnel shall be treated as PWs: Persons belonging, or having belonged, to the armed forces of the occupied country, if --
Figure 1-3. Definition of prisoner of war (GPW). Obviously, there are many personnel who qualify for and require treatment as PWs. If there is any question whether a person should be treated as a PW, treat the individual as such. The determination whether an individual qualifies as a PW is a Staff Judge Advocate (SJA) function, but has a direct impact on the interrogation effort due to GPW requirements. It is especially important in LICs to distinguish between PWs and criminals. PERTINENT ARTICLES OF GENEVA CONVENTIONS Several articles of the GPW apply to interrogators and interrogation operations. The articles most commonly used by interrogators are shown in Figure 1-4. The interrogator encounters many sources who vary greatly in personality, social class, civilian occupation, military specialty, and political and religious beliefs. Their physical conditions may range from near death to perfect health; intelligence levels may range from well below average to well above average; and security consciousness may range from the lowest to the highest.
Figure 1-4. Pertinent articles of the GPW. Sources may be civilian internees, insurgents, EPWs, defectors, refugees, displaced persons, and agents or suspected agents. Because of these variations, the interrogator makes a careful study of every source to evaluate his mental, emotional, and physical state, and uses it as a basis for interrogation. He deals mainly with three categories of sources: cooperative and friendly, neutral and nonpartisan, and hostile and antagonistic. A cooperative and friendly source offers little resistance to interrogation, and normally speaks freely on almost any topic introduced, other than those which tend to incriminate or degrade him personally. To obtain the maximum amount of information from cooperative and sources, the interrogator takes care to establish and preserve a friendly and cooperative atmosphere by not inquiring into those private affairs which are beyond the scope of the interrogation. At the same time, he must avoid becoming overly friendly and losing control of the interrogation. A neutral and nonpartisan source is cooperative to a limited degree. He normally takes the position of answering questions asked directly, but seldom volunteers information. In some cases, he may be afraid to answer for fear of reprisals by the enemy. This often is the case in LIC where the people may be fearful of insurgent reprisals. With the neutral and nonpartisan source, the interrogator may have to ask many specific questions to obtain the information required. A hostile and antagonistic source is most difficult to interrogate. In many cases, he refuses to talk at all, and offers a real challenge to the interrogator. An interrogator must have self-control, patience, and tact when dealing with him. At lower tactical echelons, there is generally insufficient time available to effectively interrogate a hostile or antagonistic source. When time is available, and the source appears to be an excellent target for exploitation, the source should be segregated and approached in an effort to obtain his cooperation. Because of possible high stress and frustration levels that such a source may invoke in you, great care must be taken to maintain your self-control. No matter what the source says or does, you must abide by the provisions of the law of war as previously discussed. The absence of the use of threats in interrogation is intentional, as threats in and of themselves constitute a form of coercion. Any attempt at enforcement of a threat would constitute an act prohibited by the GWS, GPW, or GC and is punishable under the UCMJ. A hostile or antagonistic source may be best exploited at echelons where sufficient time and resources will generally be available. The successful interrogator is a skilled professional who is able to rapidly evaluate sources of information and adapt his approaches and techniques accordingly. The interrogator extracts intelligence from two primary sources: human sources and material sources (primarily CEDs). The senior interrogator determines which of these sources may be most effectively exploited to meet the supported commander's PIR and IR. CEDs (see Chapter 4) include any piece of recorded information which has been in the possession of a foreign nation and comes into US possession. This includes US documents which the foreign nation may have possessed. There are many ways to acquire a document; some are found in the possession of human sources, on enemy dead, or on the battlefield. There are three types of documents:
An interrogator should possess an interest in human nature and have a personality which will enable him to gain the cooperation of a source. Ideally, these and other personal qualities would be inherent in an interrogator; however, in most cases, an interrogator can cultivate these qualities if he has the desire and is willing to devote time to study and practice. Some desirable personal qualities in an interrogator are discussed below. Motivation is the most significant factor to achieve success. Without motivation, other qualities lose their significance. The stronger the motivation, the more successful the interrogator. An interrogator may be motivated by several factors; for example:
The interrogator must be constantly aware of the shifting attitudes which normally characterize a source's reaction to interrogation. The interrogator --
The interrogator must have patience and tact in creating and maintaining rapport between himself and the source, thereby enhancing the success of the interrogation. The validity of the source's statements and motives behind these statements may be obtainable only through exercise of tact and patience. Displaying impatience may --
An interrogator, with patience and tact, is able to terminate an interrogation and later continue it without arousing apprehension or resentment. The interrogator must maintain credibility with the source and friendly forces. Failure to produce material rewards when promised may adversely affect future interrogations. The importance of accurate reporting cannot be overstressed, since interrogation reports are often the basis for tactical decisions and operations. The interrogator must maintain an objective and dispassionate altitude, regardless of the emotional reactions he may actually experience or simulate during the interrogation. Without objectivity, he may unconsciously distort the information acquired. He may also be unable to vary his interrogation techniques effectively. The interrogator must have exceptional self-control to avoid displays of genuine anger, irritation, sympathy, or weariness which may cause him to lose the initiative during the interrogation. Self-control is especially important when employing interrogation techniques which require the display of simulated emotions or attitudes. An interrogator must adapt to the many and varied personalities which he will encounter. He should try to imagine himself in the source's position. By being adaptable, he can smoothly shift his techniques and approaches during interrogations according to the operational environment. In many cases, he has to conduct interrogations under unfavorable physical conditions. A tenacity of purpose can be the difference between an interrogator who is merely good and one who is superior. An interrogator who becomes easily discouraged by opposition, noncooperation, or other difficulties will neither aggressively pursue the objective to a successful conclusion nor seek leads to other valuable information. The interrogator's personal appearance may greatly influence the conduct of the interrogation and altitude of the source toward the interrogator. Usually a neat, organized, and professional appearance will favorably influence the source. A firm, deliberate, and businesslike manner of speech and altitude may create a proper environment for a successful interrogation. If the interrogator's manner reflects fairness, strength, and efficiency, the source may prove cooperative and more receptive to questioning. However, depending on the approach techniques (see Chapter 3), the interrogator can deliberately portray a different (for example, casual or sloven) appearance and demeanor to obtain the cooperation of the source. Achieving and maintaining the initiative are essential to a successful interrogation just as the offense is the key to success in combat operations. The interrogator must grasp the initiative and maintain it throughout the interrogation. The source, especially if detained by military forces during tactical operations, normally has undergone a traumatic experience and fears for his life. This anxiety is usually intensified by the source's lack of knowledge and understanding of what is about to occur (fear of the unknown), or by the unfounded fear he will be tortured or executed. The interrogator has a position of authority over the source. The source realizes this fact, and, in some cases, believes his future might depend upon his association with the interrogator. The interrogator must be knowledgeable on a variety of subjects in order to be effective in exploiting sources. Some of these areas are --
In addition to these subjects, the interrogator should have a knowledge of basic psychology and neurolinguistics. PROFICIENCY IN THE TARGET LANGUAGE The interrogator must be proficient in one or more foreign languages to exploit both human sources and CEDs. According to the GPW, a prisoner must be questioned in a language he understands. The more proficient an interrogator is with the target language, the better he will be able to develop rapport with his source, understand the nuances of the source's speech, and follow up on source leads to additional information. The skilled linguist will be able to translate CEDs quicker and more accurately than the interrogator who is merely familiar with the target language. KNOWLEDGE OF THE TARGET COUNTRY The interrogator should be familiar with the social, political, and economic institutions; geography; history; language; and culture of the target country. Since many sources will readily discuss nonmilitary topics, the interrogator --
The interrogator should understand US law of war obligations contained in the GWS, GPW, and GC regarding the treatment of EPWs, retained personnel, and civilian internees (see Figure 1-4). The interrogator should be familiar with the capabilities, limitations, and employment of standard weapons and equipment so he may recognize and identify changes, revisions, and innovations. Some of the more common subjects of interest to the interrogator include the following:
ARMED FORCES UNIFORMS AND INSIGNIA Through his knowledge of uniforms, insignia, decorations, and other distinctive devices, the interrogator may be able to determine the rank, branch of service, type of unit, and military experience of a military or paramilitary source. This knowledge is helpful during the planning and preparation and the approach phases discussed in Chapter 3. OB is defined as the identification, strength, command structure, and disposition of personnel, units, and equipment of any military force. Interrogation OB elements are separate categories by which detailed information is maintained. They are --
During the questioning phase, OB elements assist the interrogator in verifying the accuracy of the information obtained and can be used as an effective tool to gain new information. Aids which may be used to identify units are --
UNDERSTANDING BASIC PSYCHOLOGY An interrogator can best adapt himself to the EPW's or detainee's personality and control of the their reactions when he understands basic psychological factors, traits, attitudes, drives, motivations, and inhibitions. For example, the timely use or promise of rewards and incentives may mean the difference between an interrogation's success or failure and future EPW or detainee exploitation. Neurolinguistics is a behavioral communication model and a set of procedures that improve communication skills. The interrogator should read and react to nonverbal communications. An interrogator can best adapt himself to the source's personality and control his own reactions when he understands basic psychological factors, traits, attitudes, drives, motivations, and inhibitions. INTERROGATOR CAPABILITIES AND LIMITATIONS HUMINT collection is capable of obtaining information pertinent to all six IEW tasks:
Interrogators are trained as linguists to question EPWs and civilian detainees and to exploit CEDs. During their collection, interrogators attempt to obtain and report any information possessed by these targets that pertains to the IEW tasks. This persistence is determined by comparing the information obtained to the SIR contained in the interrogation element's collection mission. Interrogators are capable of collecting information on political, economic, and a wide range of military topics. For the most part, interrogators attempt to organize their collection effort according to the OR elements analysts use. In addition to these elements, interrogators also obtain PIR-directed information on the missions assigned to enemy units. Appendix B discusses relevant questioning guides. The environment in which interrogation operations are performed affects the degree of success achieved. There are primarily two areas, both having limitations, upon which the interrogators depend:
If the IEW process or combat operations are not ideal, use what you can to capitalize on capabilities. The IEW process can limit interrogators by assigning collection missions which are not suited to HUMINT collection capabilities; as well as by not disseminating copies of the following reports:
Combat operations can limit interrogators by --
Interrogation operations are also limited by the very nature of HUMINT collection. EPWs or detainees and CEDs must actually have the desired information before interrogators can collect it. With EPWs or detainees, there is always the possibility knowledgeable individuals may refuse to cooperate. The UCMJ, GWS, GPW, and GC set definite limits on measures which can be taken to induce an EPW or detainee to cooperate. HICs are conflicts between two or more nations and their respective allies, where the belligerents employ modern technology complemented by intelligence; mobility; firepower (to include NBC weapons); service support; and C3 resources. MICs are conflicts between two or more nations and their respective allies, where the belligerents employ modern technology complemented by intelligence; mobility; firepower (without NBC); C3; and service support resources for limited objectives under definitive policy limiting employment of destructive power and geography involved. LICs are political-military confrontations between contending states or groups below conventional war and above the routine, peaceful competition among states. They --
LIC operational intelligence requirements are HUMINT intensive and demand detailed familiarity with the military, political, and front organizations of the insurgent enemy, and the environment in which he operates. The Interrogator's familiarity with the areas of operations (AOs) must include an understanding of the insurgency, its objectives, history, successes, and failures. This understanding is required not only on a general countrywide basis but also on an expanded basis within the interrogator's particular AO. Therefore, it is essential the interrogator grasps the importance the insurgent organization places on accomplishing political objectives as opposed to military successes. One measure of the interrogator's effectiveness is his ability to apply appropriate interrogation techniques to the personality of the source. Interrogations associated with LIC operations dictate the need for skill in the full range of interrogation techniques so the interrogator can conduct the many types of interrogations demanded. Warfighting doctrine IEW principles apply for LIC; however, intelligence indicators for insurgent activity are unique, Anything insurgents can do to influence and direct a society toward overthrowing its government is reflected by some action or indication, no matter how subtle. Some MI advisors may be required to assist paramilitary and nonmilitary elements in developing HUMINT sources and exploiting their information. As US forces are committed to the LIC operation, interrogation support will more closely adhere to the traditional tactical environment. Typical LIC missions are --
HUMINT is a major LIC source because of the necessity to exploit the local populace and to know and understand enemy intentions, In LIC, interrogators exploit EPWs and CEDs, For example, in addition to conducting EPW operations at collecting points, interrogators may participate in cordon and search and roadblock operations, tactical check points, and low-level collection missions in conjunction with the supporting CI unit (see PM 34-60A(S)). Interrogators may also provide support to drug and law enforcement agency (DLEA) operations. Interrogators perform various types of missions. As discussed previously, the two main missions are personnel and document exploitation, There are other functions for which interrogators are ideally suited because of their language and HUMINT training, These include --
DRUG AND LAW ENFORCEMENT AGENCY OPERATIONS Army interrogators may assist Federal law enforcement authorities and, where lives are endangered, state and local law enforcement authorities, after concurrence by the Army General Counsel and approval by the Secretary of Defense or his designee. (See AR 381-10, Procedure 12, and AR 500-51.) Army interrogators may assist law enforcement agencies and security services or foreign governments or international organizations only in accordance with applicable law and policy, including any status of forces agreements. Such assistance will ordinarily constitute security assistance, which must be approved in accordance with AR 12-15, Under no circumstances will interrogators assist any law enforcement authorities in any manner without prior approval by competent authority after a legal review of the proposal.
|